Recently the Ponemon Institute presented their “2021 State of Industrial Cybersecurity” report which was sponsored and published by Dragos Inc. For this research Ponemon surveyed over 600 IT and OT security practitioners divided over a wide variety of industries. This article covers some of their most interesting key findings and recommendations and how these match Secura’s OT security lifecycle. The full report is published here.
Ponemon 2021 State of Industrial Cybersecurity
03 December 2021 |
Author(s):
 Frank Ruedisueli - Senior OT Security Consultant
Frank Ruedisueli - Senior OT Security Consultant
Security Incidents
According to this research 63% of the respondents indicated that their organization had at least one OT/ICS cybersecurity incident in the past two years. At the same the researchers noted that both the frequency and severity of cyber-attacks are increasing. The average cost of such an incident is about 3 million USD. This calculation includes downtime, replacement of equipment, fines and labour costs of IT and OT security personal.
This research also uncovered some additional statistics. For instance, the average detection time of an incident is 170 days. After detection the severity and impact must be analysed by security experts, and this takes on average another 66 days. Finally, it takes 80 days to remediate the cybersecurity incident making it to a total of 316 days from initial detection to remediation. This still excludes any additional post incident activities or additional preparation steps to prevent similar incidents in the future.
One of the most prevalent and devastating cyber-attacks is ransomware. The study indicated that 29% of the participants stated that their organization had do deal with such an attack. In half of these cases the ransom paid was over $500.000.
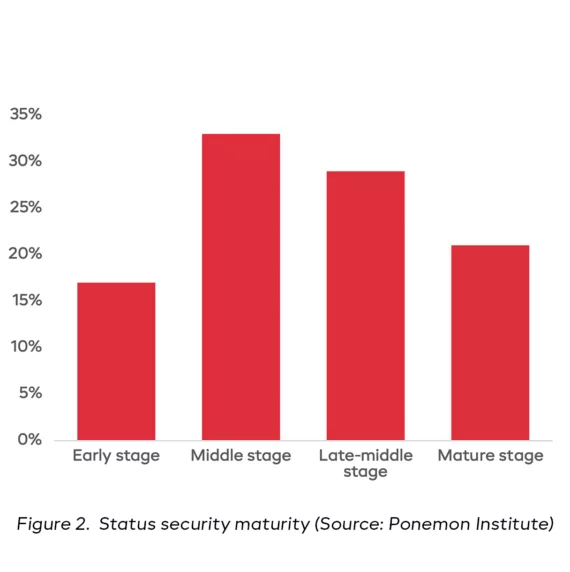
Security Maturity
Only 21% of the participants reported that their OT/ICS cyber security program security reached full maturity while about 50% is still at an early or middle stage. This means that many security program activities have not yet been planned or deployed and the organization might not be in control of their cyber security risk. In a mature organization the efficiency and effectiveness of their cyber security program is continuously measured and together with the current cyber security risks, communicated to top-level management. At the same time management provide sufficient budget and resources to keep the program running and reduce cyber risk to an acceptable level.

Conclusions and Recommendations
One of the main recommendations is to overcome the cultural and technical differences between the IT and OT teams. A remarkable result that explains the current blockers for investing in OT/ICS security illustrates this in a nice way because the two main findings seem to be a contradiction. One states that OT security is managed by the engineering department which does not have security expertise while the other states that OT security is managed by the IT department that is lacking engineering expertise.
An organization should have one unified security strategy, while at the same time need to understand that OT/ICS requires a different approach. A combined team is required that should also inform top level management about the status of the security program and the organizations cyber risk.
The organization should ensure there are sufficient resources and budget allocated to execute and improve cybersecurity. This starts with a detailed inventory of all attached ICS devices throughout their entire lifecycle. A second recommendation here is to develop, maintain and test a cyber incident response plan.

OT Cybersecurity Roadmap
Implementation and continuous improvement of any cybersecurity program takes time. It is important to start mapping the highest business priorities to OT processes and finally to the ICS assets to determine adequate controls and their priority. To determine this priority threat driven as consequence driven scenarios should be used. Threat driven is reasoned from an attacker’s perspective and maps possible threats to an organization that could be based on threat intelligence reports or threat modeling exercises. Consequence-driven scenarios are based on the worst possible impact that an organization wants to prevent. Both will lead to an inventory of existing, inadequate, or missing controls that are required to mitigate all these scenarios. It is now time to create a roadmap, plan for continuous improvement and start mitigating the highest priorities.
It all starts with a good understanding of the current cybersecurity posture and its potential weaknesses. This is also reflected by the 60% of the participants of this study who stated that their top priority in 2021 is to improve this by performing OT/ICS specific gap-, risk- or vulnerability assessments.

Secura’s Cybersecurity Portfolio
Altogether these recommendations fit perfectly to our cybersecurity portfolio, specifically the first category “Audit & risk assessment”.
Secura provides a variety of specific OT/ICS assessment services and have this experience in multiple (critical) industrial markets, for example oil and gas, energy and (waste)water. With a gap analysis we identify the current state of security controls according to the IEC 62443-3-3 standard. With an OT risk assessment, we use a consequence-driven approach to quantify the highest cybersecurity risks for an OT environment. For a threat-driven approach we can offer OT threat modeling exercises. Finally, we provide security maturity assessments based on ISO27000 and IEC 62443-2-1 to assess the company’s maturity level using a holistic approach covering people, process, and technology in both IT and OT.
An important part of every security program is to test if all the designed mitigation controls and processes work in practice. Here we can provide one of our most valued services, vulnerability, and penetration testing. We are fully aware of the specific considerations that apply for OT systems and have the experience to plan and perform these tests safely and know what we can do or can’t do. Of course, always in close corporation with the asset owner. The same is applicable for our Red Teaming exercises where we even go one step further and simulate a full scale cyber-attack, testing not only the technical security controls but also the detection and response capabilities of the organization.
All assessments have their place on the roadmap and are useful for companies that are in a different stage in their cybersecurity program. This is also a continuous improvement loop, where technology and cyber threats are always changing. We are happy to invite you for an intake meeting, together with our sales team and security consultants so we can determine the best approach together.
Note that our full cybersecurity service portfolio also includes security training and certification. For more information on these topics, please view our industrial market page.





