Rise of the New Version of Knight Ransomware in Hospitals

The world is alarmed by a series of ransomware attacks carried out by Ransomhub. In April alone, there were 26 reports of attacks on hospitals and other organizations such as Christie’s auction house. London hospitals had to halt blood transfusions and surgeries due to these attacks.
What is Ransomhub? It is an updated version of the ransomware program Knight. In early 2024, the source code of Knight was put up for sale on the dark web. The new owner (or possibly the same owner) has improved the program and now offers it as Ransomware-as-a-Service (RaaS). This service actively attracts affiliates. Many former users of Lockbit are switching to Ransomhub because Lockbit’s operation has recently been heavily impacted by law enforcement. The person behind Lockbit remains at large and active.
Healthcare Sector Under Fire
In the past, various RaaS operations stated that attacks on the healthcare sector were unacceptable, especially during the pandemic. However, recently, Ransomhub has been targeting healthcare institutions and their suppliers.
Double Extortion: In addition to the traditional ransomware business model, where ransom is demanded to restore access to encrypted data, criminals are now also using the “double extortion” method. They first steal data and then threaten to sell or release it publicly.
Faster Than Before: The rapid growth and development of this new RaaS service suggest that Ransomhub will play a significant role in the cybercriminal world. This is concerning because the time between initial access and the deployment of ransomware is becoming increasingly shorter.
Research from shows that since 2023, ransomware has been deployed in more than half of cases within a week. In a third of cases, it happens within 48 hours. The majority of ransomware is activated outside of working hours, often early in the morning.
Methods Used
As is common in ransomware attacks, initial access often occurs through credentials obtained via phishing or spearphishing. Therefore, it is essential that your organization continuously focuses on the cybersecurity awareness of your employees, for example, through the SAFE program.
The hackers install malware and increasingly also remote access software. Think of programs like TeamViewer, VNC, Atera, and Splashtop. They also frequently exploit known vulnerabilities in the internal network.
What Known Vulnerabilities?
We can never know exactly what the ransomware affiliates are trying. But based on our research, we can indicate what regularly goes wrong in cybersecurity in healthcare. Attackers themselves sometimes provide advice, as seen in the image below.
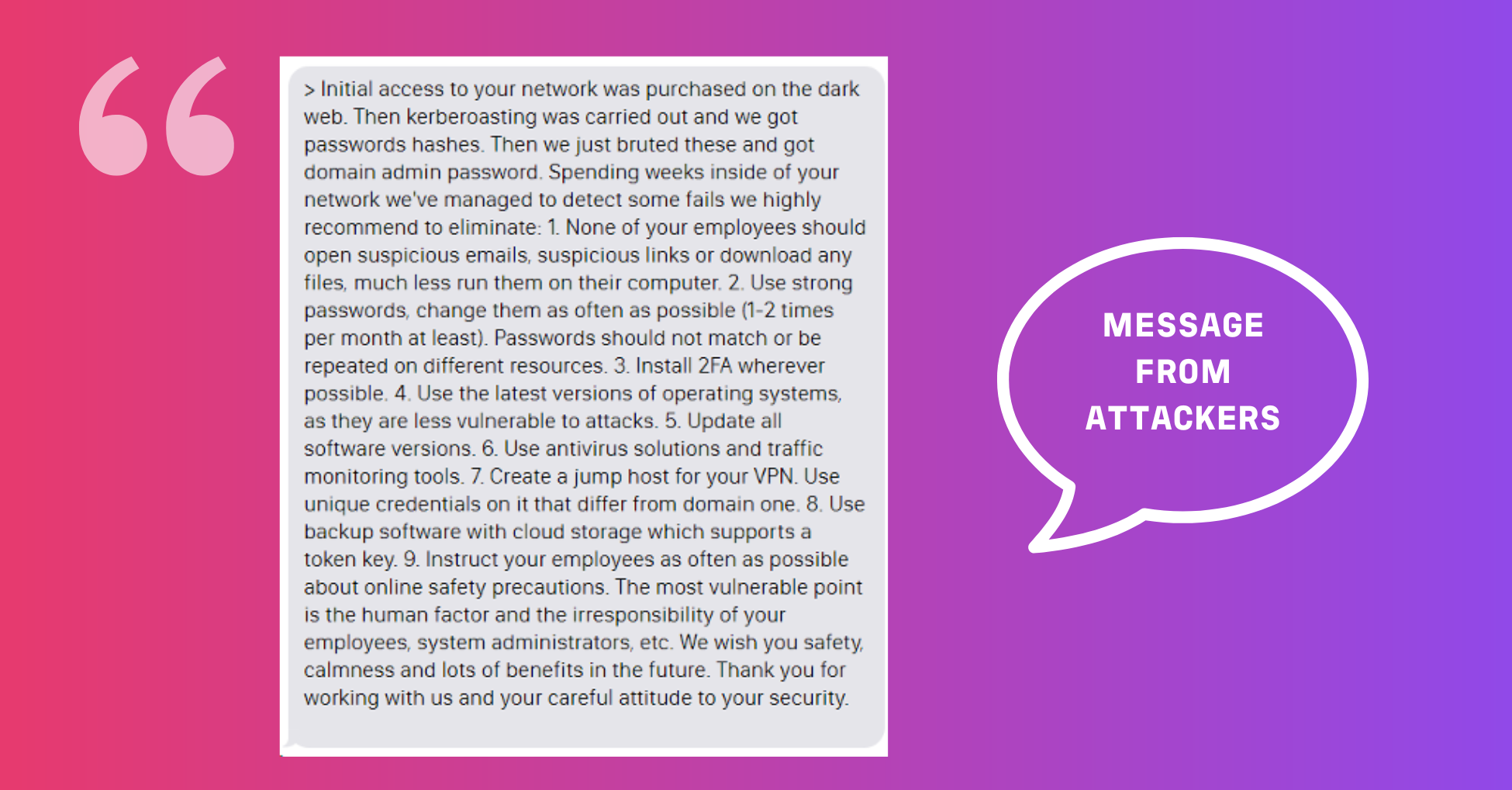
Example of a message from the attackers
Hackers often first gain access to a single system or account within the internal network. Subsequently, the intruders access other systems and accounts in the network by, for example, exploiting:
- Weak passwords and a lack of multi-factor authentication.
- So-called "null sessions" that are sometimes permitted by systems in the network, allowing limited access to the system's content without login credentials.
- A so-called "NTLM relay" attack, where legitimate login attempts can be exploited by an attacker to gain access to other systems.
- Network ports and services that are necessary only for administrators but are often also available or usable by non-administrative employees.
- Systems in the internal network that are not up to date and contain known critical vulnerabilities that can be exploited, such as zerologon.
Next Step: Obtaining the Highest Privileges
Once network access has been broadened, it often becomes possible to gain extensive or even the highest privileges within the environment through attacks such as:
- Exploiting a misconfiguration in Active Directory (the so-called ADCS templates that are standard in an AD environment), allowing the attacker to immediately gain the highest privileges in the environment.
- Obtaining high-privilege accounts through kerberoasting attacks, enabling the attacker to retrieve the password of the respective high-privilege account.
- Reading passwords or password hashes from the memory of a computer with administrative rights by dumping credentials of recently logged-in users. On server systems, this typically yields high-privilege administrator accounts, as they are the only accounts logging into such systems.
We recommend that healthcare organizations pay extra attention to the above issues to keep malicious actors at bay in the short term.
How Can Secura Help?
Secura uses a risk-based approach to assess how vulnerable your organization is to ransomware attacks: the Ransomware Resilience Assessment. Based on the identified and classified risks, we provide actionable advice to enhance your cyber resilience.
ALSO OF INTEREST TO YOU
Dark web monitoring
Awareness/phishing programs
More information
Would you like more information on increasing resilience against ransomware? Please fill out the form, and we will contact you within one business day.

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.











