(alleen beschikbaar in het Engels)
How a Malicious App Has Been Targeting FIFA Qatar Fans

Given how smartphones have basically become an extension of our hand, it is logical for people to always be looking for different applications that cover their needs. If you are a football fan and you want to stay up-to-date with the FIFA World Cup in Qatar, having an app to receive team scores and watch live matches might seem like a good idea.
In an attempt to cover that need, an application spawned on Facebook, which, on the surface, seems to be providing the score of the matches, news and even the live feed for some of the matches. However, there is something additional that the application is doing on the background, and that is, infecting the mobile device and allowing attackers to extract personal information and files.
**Disclaimer**: The application is still being distributed from the sources mentioned below. The C&C server of the application is still active. Use any of the information provided in this page at your own risk.
The application was first discovered by ESET on the 25/11/2022. There might be multiple Facebook Groups related to it similar to the one shown below.
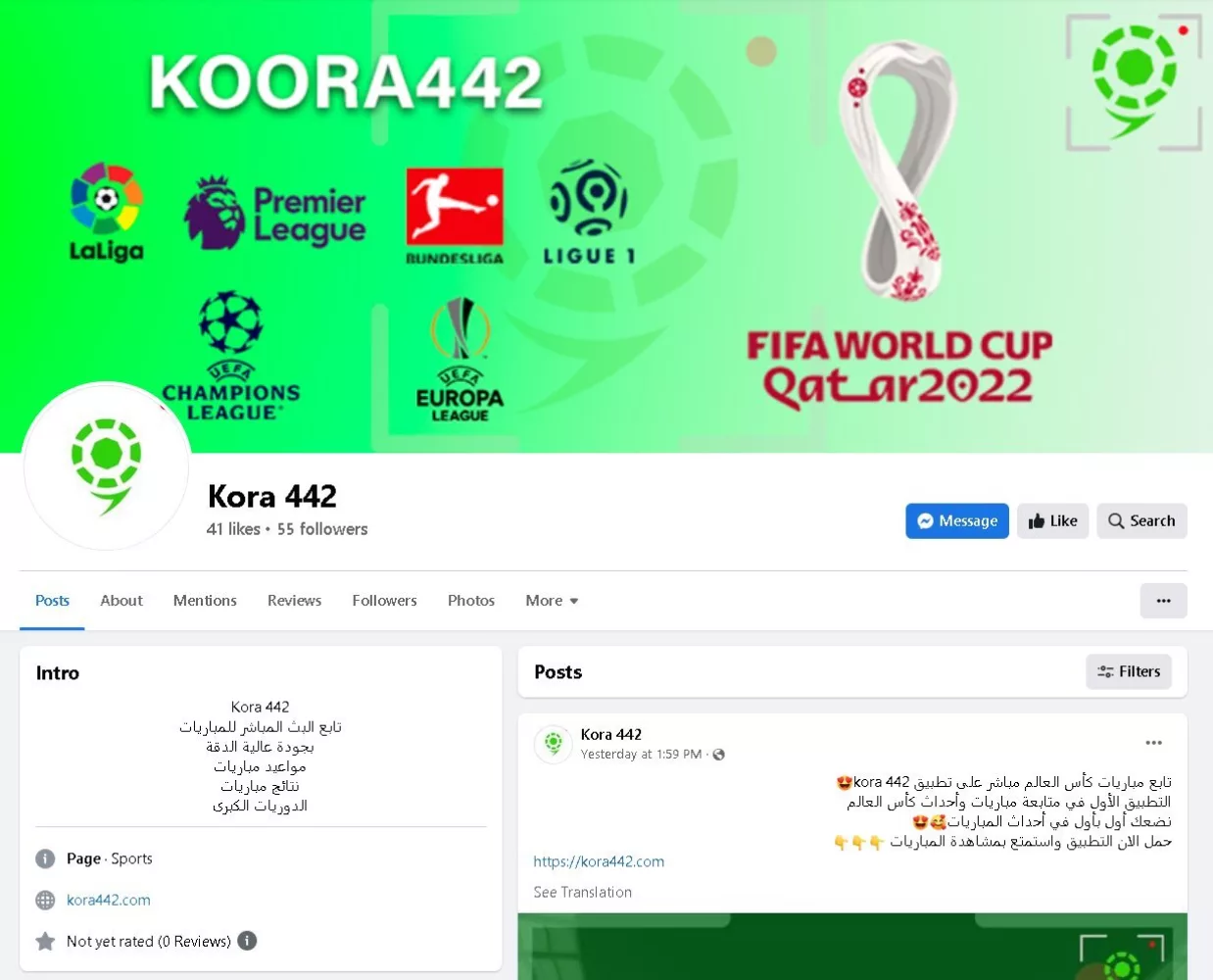
This Facebook Group and any others are merely redirecting the user to the URL *kora442[.]com* which is the main page distributing the malicious application. That webpage is still live during writing this blog post and has the following appearance.

The following are the details of the app.
Package Details
- Application Name: Kora 442
- Package Name: com.app.projectappkora
- Version code: 1
- Version Name: 1.0
- Minimum SDK: 21
- Target SDK: 21
- Sha256: 3f19efe7ea5aed42c2876683278a4afffc5a696c5ecb5dec5319ff715a673474
- Allow Backup: false
After installation we are presented with a screen with all the permissions the app requires:
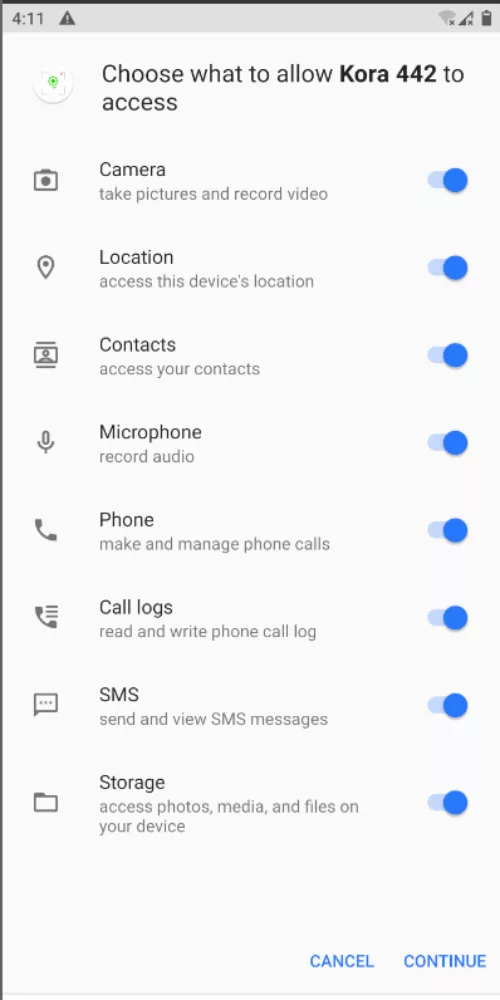
If we attempt to remove any of the permissions the following message appears:
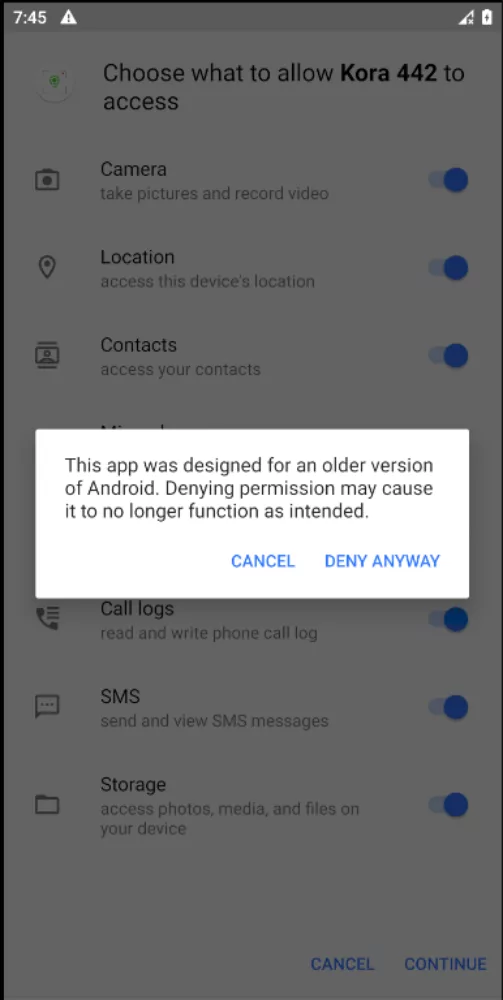
The message informs the user that if any of the permissions is denied, then the app might not function as intended. This is the reason the developers of the app decided to use as the target SDK to be the level 21. It makes it easier for the unsuspected users to accept all permissions at once and proceed from there.
The following figure shows how the app appears after installation along with some of the traffic it generates:
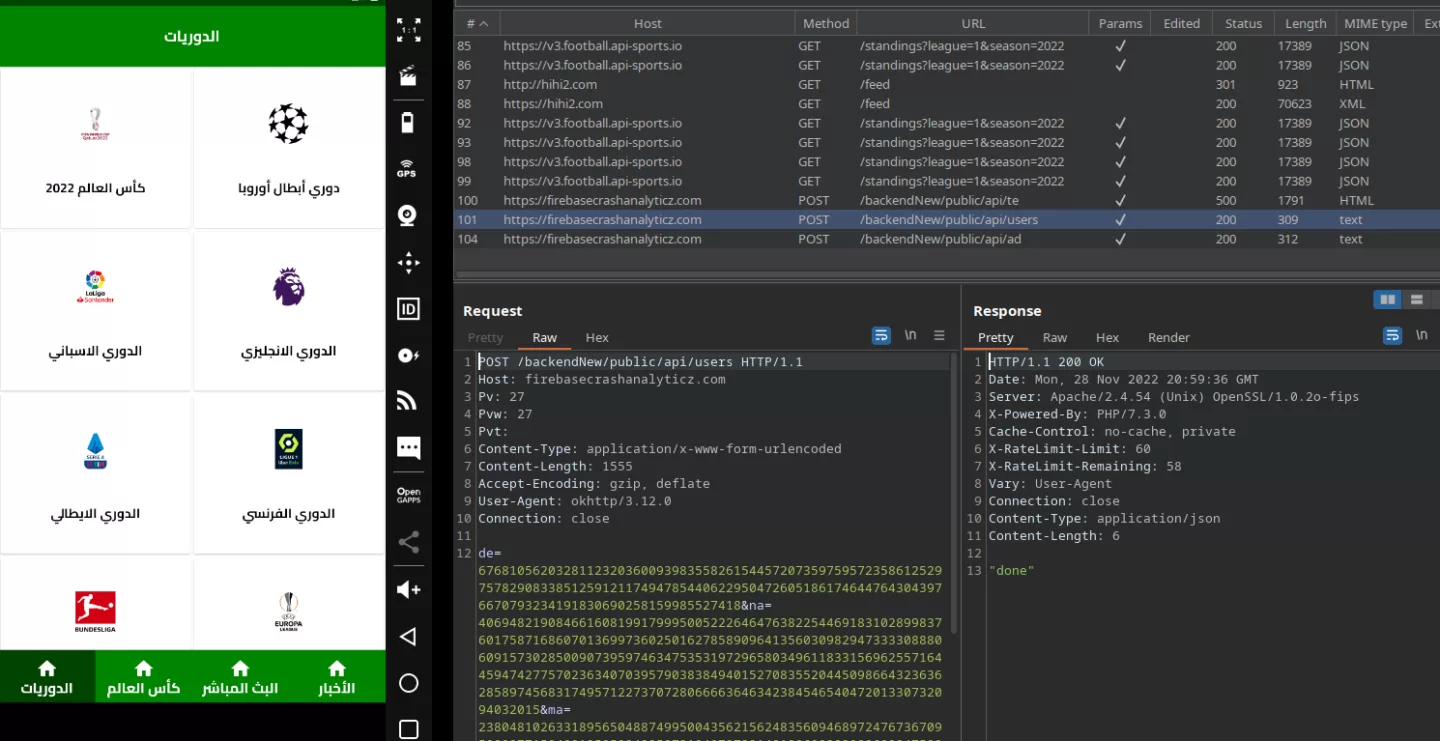
Initially when the application was installed in a virtual device no signs of malicious activity were present. Investigating this further revealed that the developers were cautious and had implemented several checks to avoid the application running in such cases. The traffic generated towards the command and controls (C&C) server (firebasecrashanalyticz[.]com) as seen in the figure above, was occurring only after bypassing these checks.
Other interesting features the application offers are the following:
- Encrypted exfiltration of files/folder
- Call/sound recording
- Access to the camera
- Running commands in shell (checking for superuser access)
Almost immediately after the users starts using the application, on the background a service starts to monitor the device. For example, the clipboard is monitored and anything copied is being saved as a temporary file in the local storage of the app, which then is being zipped and password protected and slowly uploaded to the server. The developers have done a good job remaining stealthy during the exfiltration, by avoiding parallel operations that would result in excessive resource consumption.
At the time of writing this blog post the application has already managed to infect more than 1000 users. A quick analysis on the time zone of the users infected can be seen below.
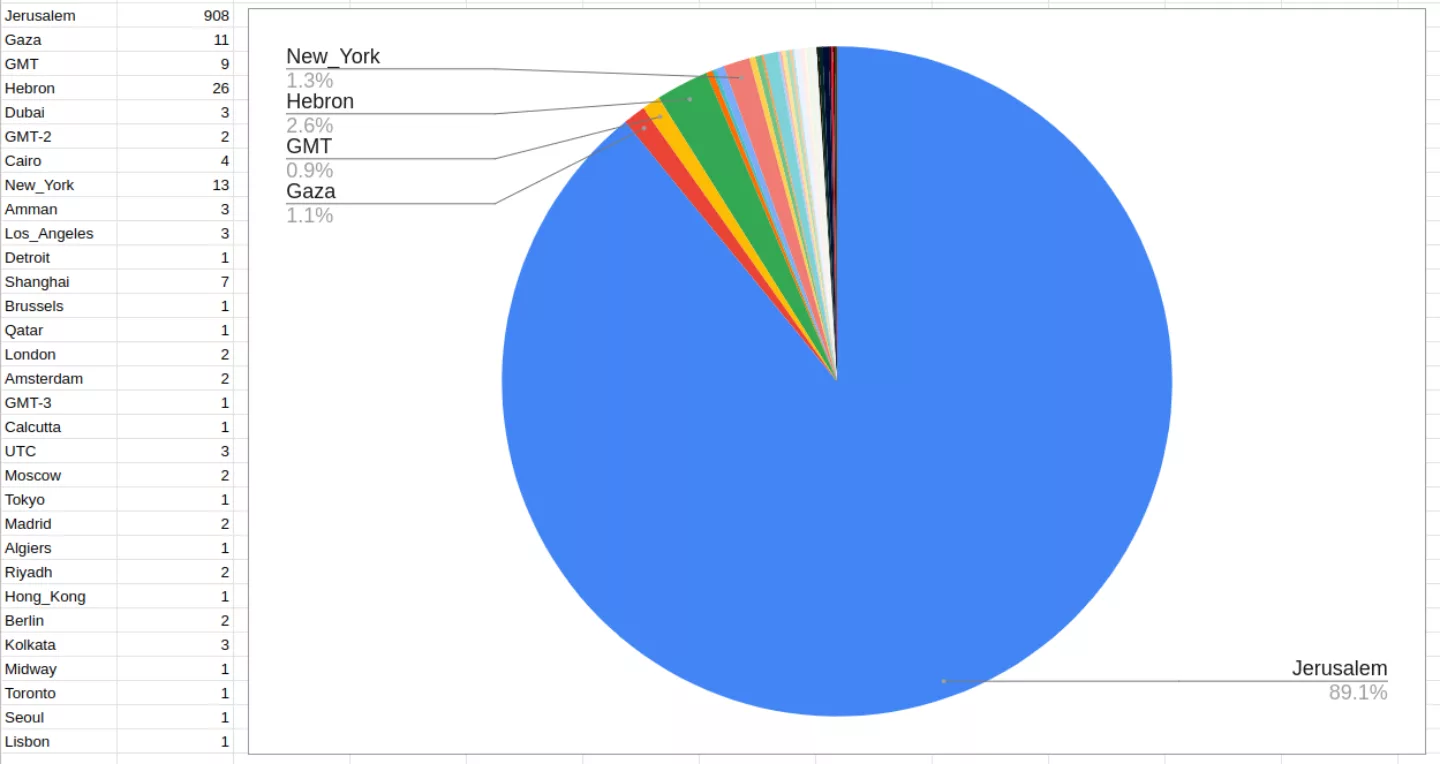
Almost 90% of the users have the time zone of "Asia/Jerusalem" which most likely means that the developers are also in the same time zone or that the infections are targeted for a region.
The number of infected users will keep rising daily until the server hosting the application and the API are terminated.
Tips to follow to spot malicious applications:
- The first and maybe the most important is, only download verified apps or apps that have a high volume of users (>100K).
- Check the comments other users have left for that app and pay attention to the 1/2-star ones.
- If an application asks you for an excessive amount of permissions, be on high alert about it.
- Be on alert for behavior that is unusual, like pop-up advertisements that you did not have before.
- Check for unusual data usage. Like in the case of the app we saw above, after all the uploading of the files would be completed we should notice it in the data usage.
- And last but not least, consider using a security app that would keep the defenses up for you.
If you have any questions about this blog, feel free to contact us.





