Background
A Trusted Platform Module (TPM) typically refers to a dedicated secure cryptoprocessor conforming to the ISO/IEC 11889 standard by the Trusted Computing Group (TCG). TPMs can be used for various purposes, ranging from platform integrity and FDE support to storage of key material and credentials (such as for SSH authentication). TPMs can be used in various platforms ranging from servers and laptops to cloud-connected IoT devices.
Two main versions of the standard exist, TPM 1.2 and TPM 2.0, with the latter not being backward compatible with the former. TPMs can be implemented in a variety of manners (with dTPMs and fTPMs being the most common):
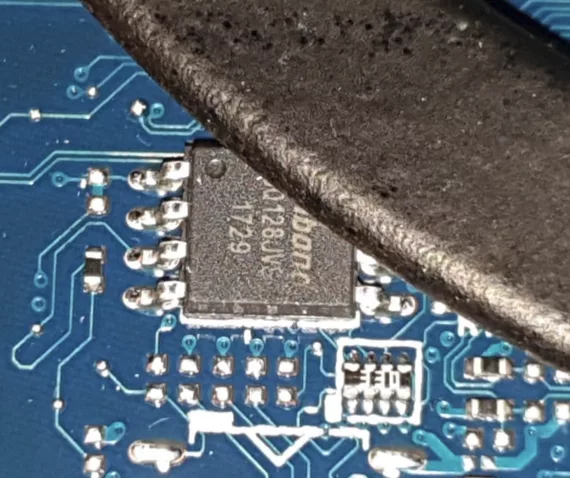
- Discrete TPMs (dTPM): which come in the form of a dedicated, tamper-resistant chip.
- Integrated TPMs: which are implemented as a hardware subsystem within a different chip.
- Firmware TPMs (fTPMs): which are firmware-based and typically run in a CPU's Trusted Execution Environment (TEE).
- Hypervisor TPMs (vTPMs): which are segmented away from a virtual machine by running on top of a hypervisor.
- Software TPMs: which are purely software-based and the least secure implementation.
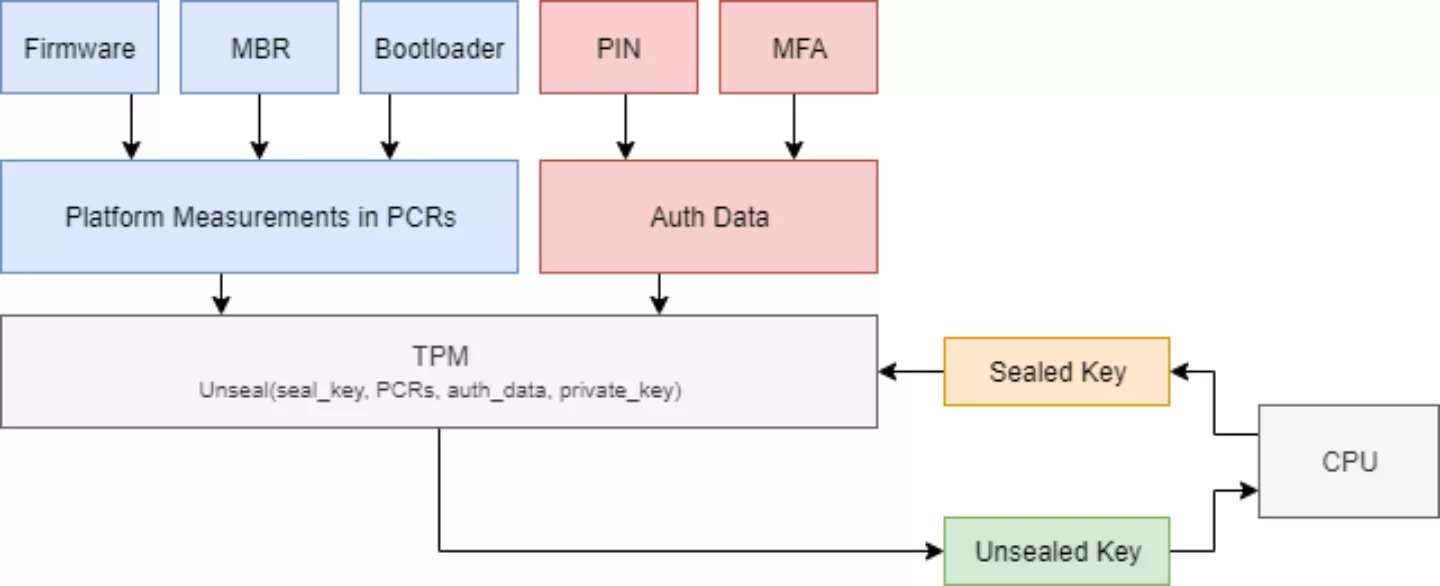
For platform integrity, TPMs provide mechanisms to support measured boot. Starting from a Core Root of Trust for Measurement (CRTM) (e.g., boot ROM of some SoC), hashes are calculated of various platform components (e.g., BIOS/UEFI, bootloader, embedded controller firmware, etc.) and stored in Platform Configuration Register (PCR) slots. This information can be incorporated into the secure boot process (possibly as part of FDE) to ensure these various components have not been tampered with.
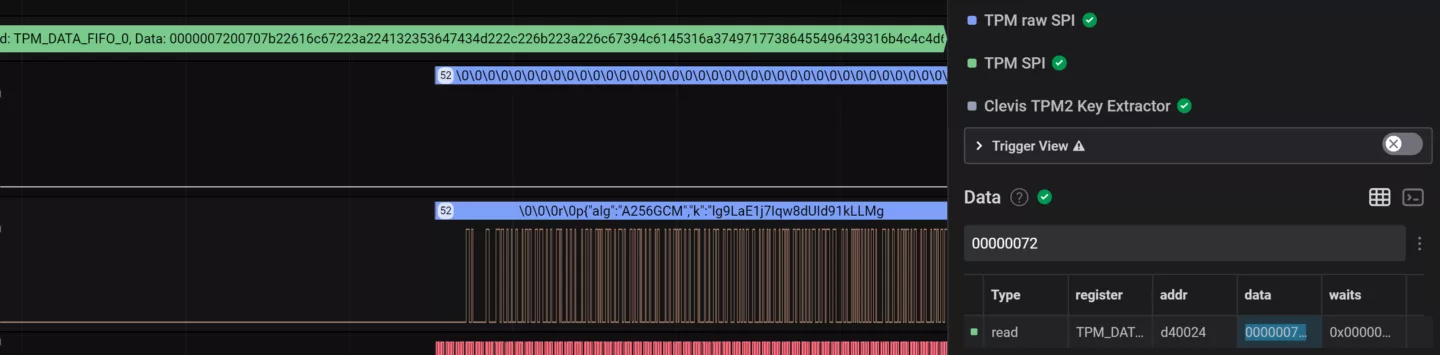
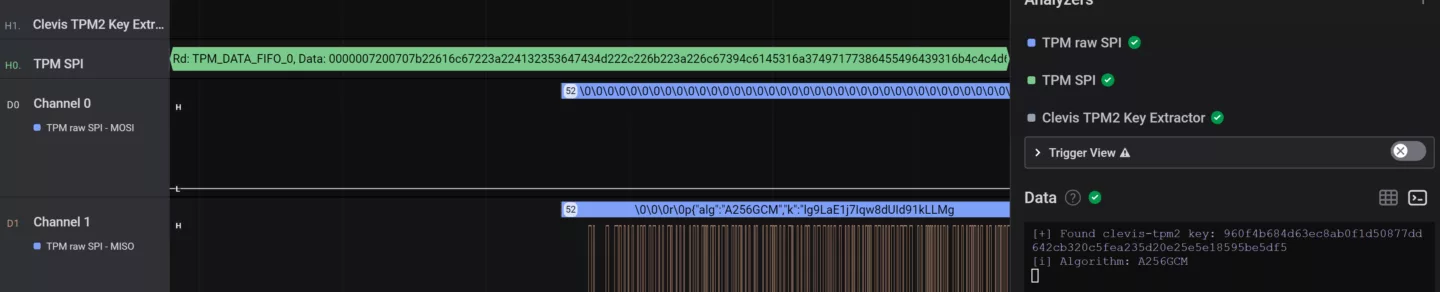
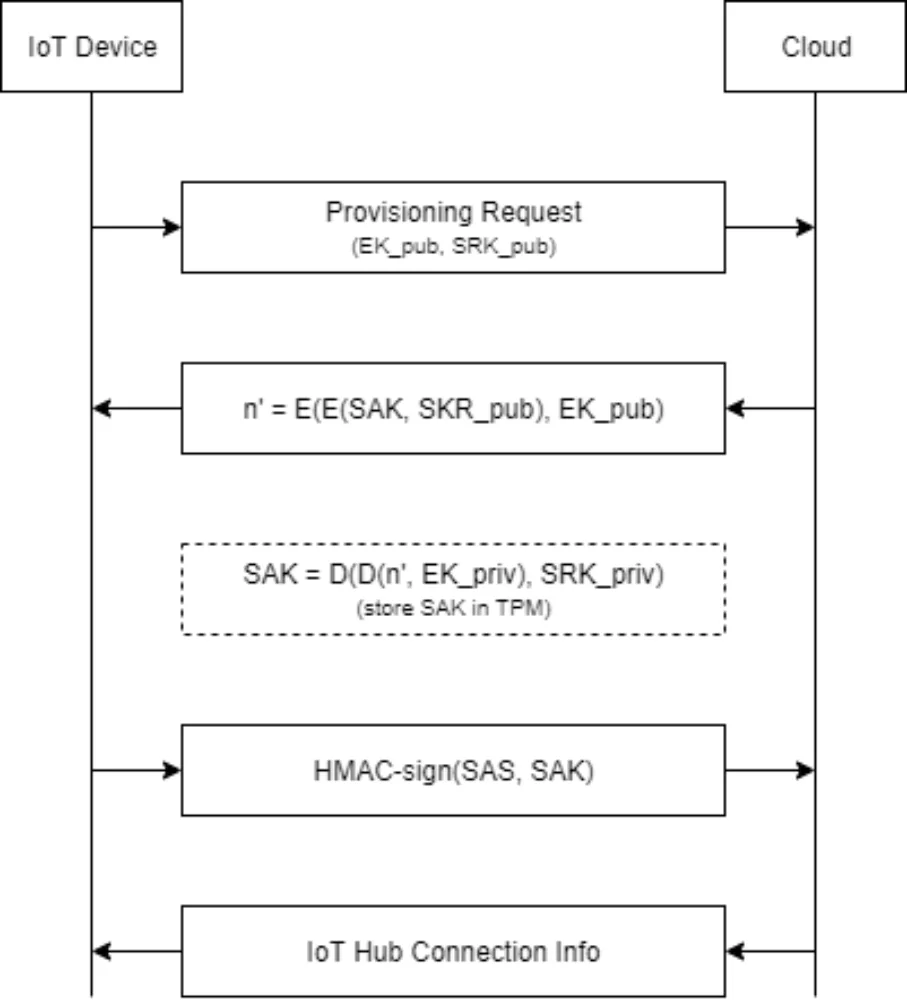
TPMs also provide mechanisms to support encryption solutions to provide confidentiality and integrity authentication guarantees. These mechanisms include key generation, the ability to encrypt key material with a TPM-specific key, and tamper-resistant features to make the TPM function as a secure storage for secrets. Using a TPM-protected key by itself is typically referred to as binding while adding measured boot PCR values into the cryptographic mix is typically referred to as sealing.
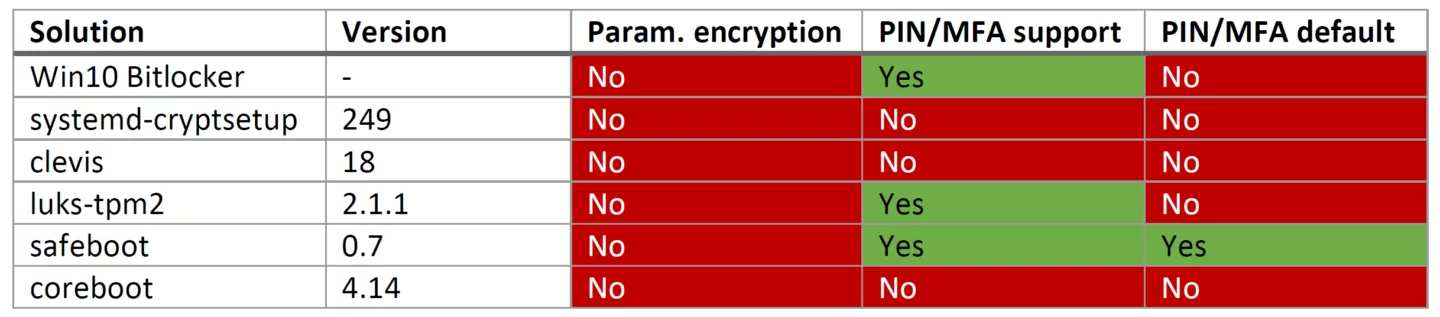
In encryption scenarios, TPMs can typically be configured in one of several modes:
- TPM only: here, the TPM automatically supplies the key to the encryption solution upon request (e.g., on boot).
- TPM + PIN: here, the TPM needs a system-supplied secret (typically a PIN entered by the user) before it will unseal the key.
- TPM + PIN + MFA: here, an additional factor, such as a USB key with a secret or TOTP, is required.
In the case of FDE, additional secrets have to be provided pre-boot. Tamper-resistant features on the TPM (ought to) prevent brute-forcing of PINs, extracting private keys, and glitching to bypass these features.
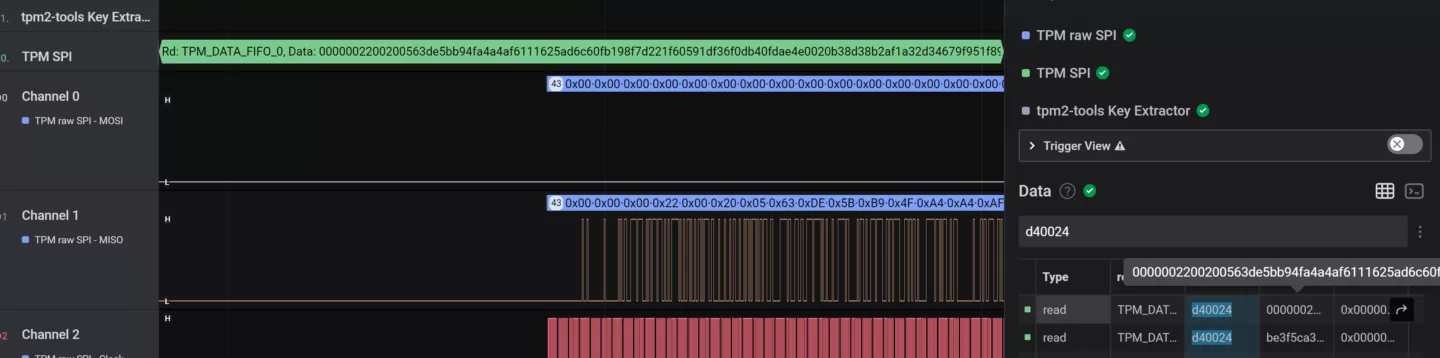
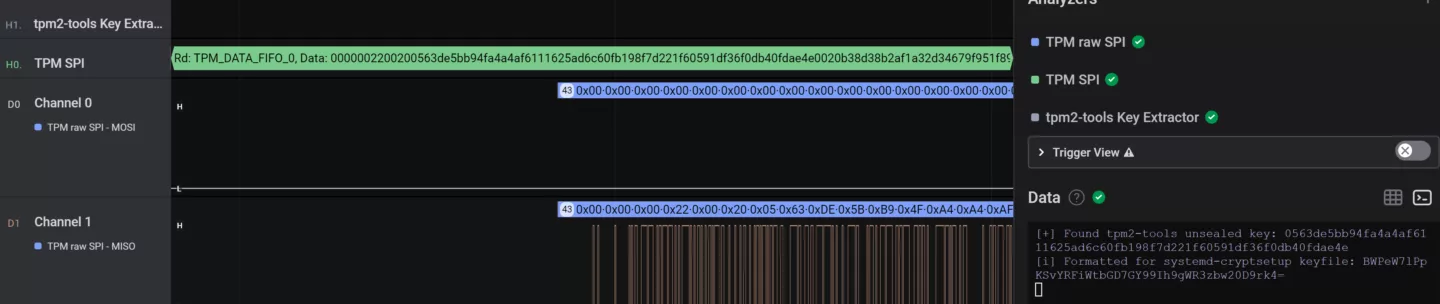
While there have been invasive probing, various side-channel, interposer, and design and implementation attacks on TPMs in the past, we will only focus on sniffing attacks against dTPMs in FDE support scenarios in this post since these types of attacks are inherent to the design of dTPMs.
Since dTPMs are dedicated chips separate from the main CPU and other controllers on a device, they need some way to communicate with them. The standard specifies the LPC, I2C, and SPI busses for this purpose, and the dTPM will have to be put on a bus together with any device that might need to talk to it (depending on whether there are single- or multi-master roles).






 Jos Wetzels - Principal Security Consultant
Jos Wetzels - Principal Security Consultant