External Attack Surface Assessment - EASA
Secure your organization from hidden threats with an External Attack Surface Assessment and gain peace of mind.
> IT | PENTESTING & MORE > External Attack Surface Assessment
What is an External Attack Surface Assessment and why is it important?
Criminal hackers are trying to access your network, and they use anything they can find, from hacked passwords to unmanaged applications. Are you aware of the data leaks and passwords from your organization that are out there on the internet or dark web?
External Attack Surface Management will help you reduce your attack surface and give you peace of mind.

Watch the video with Paul Pols, Principal Security Specialist at Secura/Bureau Veritas (1:42 min)

REVEAL HIDDEN EXPOSURES

KNOW YOUR WEAKNESSES

RAISE YOUR CYBER RESILIENCE

YOUR CHALLENGES AS A CISO
- How to ensure you have a complete inventory of your exposed assets, for example open S3 buckets, hard-coded passwords in Github, exposed SSH interfaces and unsecured Api's and IoT devices.
- How to monitor for compromised credentials on the dark web
- How to keep an eye on missing patches, outdated software and configuration issues.
You'd be surprised
Many companies are surprised to discover what can be found about them from sources on the internet. Whether you are a public organization, or a business, hackers are trying to get access to your network, and they use anything they can find. Gartner estimates that less than 1% of organizations have a proper visualization of their exposed assets.
Not only hacked passwords and unmanaged or legacy applications pose a threat to your digital security. Often we find forgotten, hardcoded passwords in repositories such as Github, or sensitive information in Amazon S3 buckets. Or we notice the use of unsecured APIs or exposed databases without proper authentication.
All those exposures and sensitive information are a treasure trove for attackers seeking to find a hole in your network defense. That's why you need External Attack Surface Management.
Also watch this presentation on External Attack Surface Management.
What is External Attack Surface Management?
External Attack Surface Management (EASM) is the process of discovering and mitigating vulnerabilities in systems that are connected to the internet. This includes assets like websites, management interfaces, IoT devices, web applications, payment gateways and cloud services. You can reduce the risk of cyber attacks by proactively identifying and addressing vulnerabilities in these external-facing systems. This will help to improve your cyber resilience.
Penetration tests and password updates are not enough to keep your organization safe from hackers. The game has changed. That's why you should proactively scan for weaknesses, exposures and vulnerabilities on the perimeter of your organization, and beyond that.
With External Attack Service Management you can:
- Reveal hidden cybersecurity exposures outside of your organization, so you can mitigate them.
- Know your weaknesses and prioritize actually exploitable vulnerabilities.
- Raise your cyber resilience.

Watch the video of Principal Security Specialist Paul Pols explaining the External Attack Surface Assessment (1:42 minutes)
How we support you
Secura helps large and medium sized organizations all over Europe raise their cyber resilience. We know the importance of External Attack Surface Management, and we know how to do this.
- Highly qualified security specialists
Secura employs highly qualified ethical hackers, forensic specialists and OSINT-specialists who are experienced in attack surface assessments. They perform thousands of security assessments each year.
- Peace of mind
External Attack Surface management will help you reduce your attack surface. This means you can bring your security risks down to a level that delivers you peace of mind and builds trust with your stakeholders.
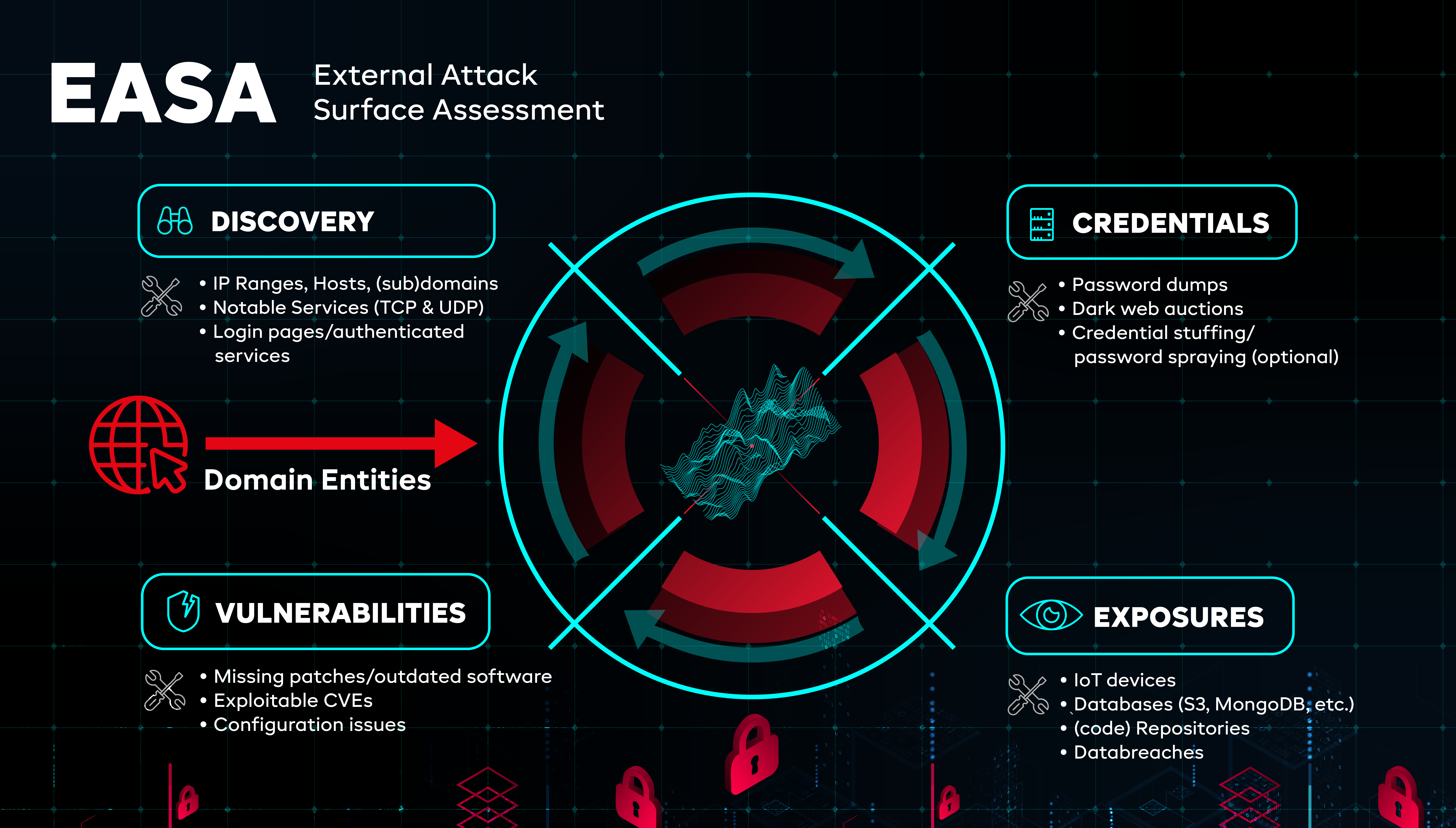
Four areas of focus in Attack Surface Management
01
Asset Discovery
Discover what assets in your organization are accessible by external parties through the internet. We will assess the risks associated with those assets.
- IP Ranges
- Hosts, subdomains
- Notable Services
- Login pages/authenticated services
02
Exposures Scan
Perform a scan for exposures and data leaks. Examples include:
- Open S3 buckets on Amazon Web Services.
- Exposed management interfaces, like login pages for administrators or SSH interfaces.
- Exposed databases without proper authentication.
- Unsecured APIs.
- Hard coded passwords and administrator keys in repositories such as Github.
- Unsecured IoT devices
03
Credentials Scan
Search on the internet and on the dark web what credentials are dumped, traded or for sale for your organization. How were those usernames and passwords obtained? You might have to disable specific endpoints or users.
- Password dumps
- Dark web
- Credential stuffing/password spraying
04
Vulnerabilities Scan
Scan for common vulnerabilities in external infrastructure. Examples include:
- Missing patches/outdated software
- Exploitable Common Vulnerabilities and Exposures (CVE’s )
- Configuration issues
How to get started with External Attack Surface Management
By now, you should be aware of the risks of sensitive information on the internet or dark web, exposures and vulnerabilities. And the need to take action proactively. But how do you get started? The way to do this is by first performing our External Attack Surface Assessment (EASA).
One time full-scope scan
Secura will do a full-scope scan of the external attack surface of your company’s domains. We will investigate all four areas: assets, credentials, exposures and vulnerabilities. We use a combination of external data sources and manual scans and tests.
The assessment will give you insight into your full external attack surface. This enables you to formulate a risk mitigation strategy and reduce the risk of cyber attacks.
Watch the webinar on External Attack Surface Management

Download Fact Sheets
Contact us about the External Attack Surface Assessment
Please fill out the form below, and we will contact your within one business day.

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.







