Protect your organization with Dark Web Monitoring
Do you know if stolen credentials from your organization are sold on the dark web? We can monitor this for you so that you can take action to protect your organization.
> IT | PENTESTING & MORE > Dark Web Monitoring
Why Dark Web Monitoring?
Criminal gangs are willing to pay for stolen usernames and passwords for specific assets on the dark web. Stolen credentials can provide attackers with initial access to your network and are the main cause of security breaches. If you know that this information about your organization is for sale, you can take immediate action to protect yourself against these attacks. But how do you find out whether stolen credentials from your organization are being sold?
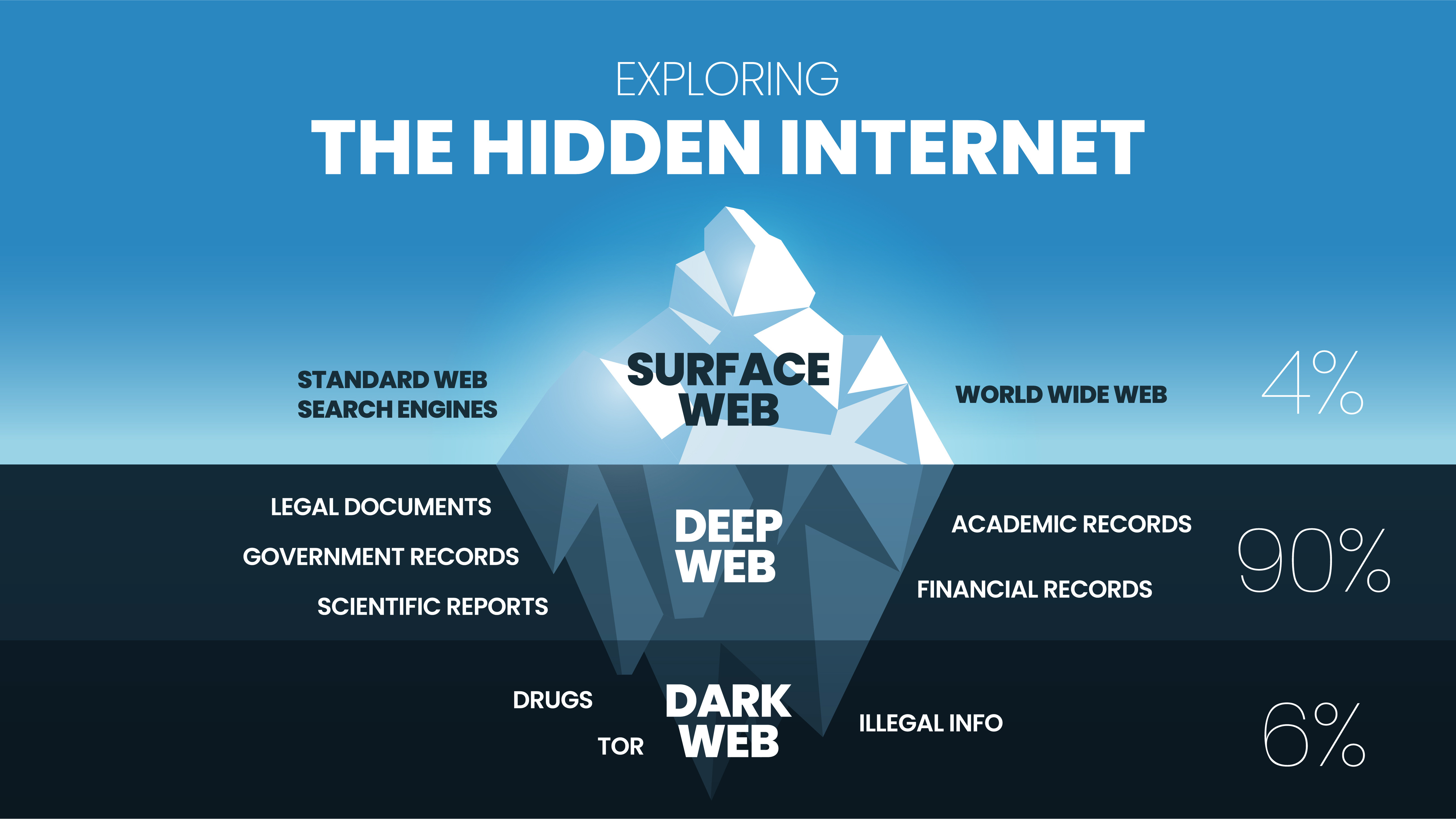
The dark web is the intentionally hidden part of the internet, that requires specific software, configurations, or authorizations to access. The most common tool to access the dark web is the Tor network. For this service, we also monitor other intentionally hidden parts of the internet, such as illegal marketplaces on the regular web and private Telegram groups.
Looking for stolen credentials
By scanning the dark web, we can discover if criminals are selling or trading in access to your assets. This means you can take immediate remediating measures, before this information is used against you. We specifically search for credentials stolen from compromised systems. These are often malware infected workstations used by employees or suppliers.
This is important, because cybercriminals can use either the stolen credentials or the compromised systems as a gateway to access the rest of your network. As such, stolen credentials and infected systems often serve as precursors to ransomware attacks. Dark Web Monitoring serves as the last line of defense - if attackers have managed to break through your other security measures, this service can give your valuable information to stop them just in time.

Watch the video of Principal Security Specialist Paul Pols explaining how Dark Web Monitoring works (1:42 minutes)

Create a last line of defense against ransomware

Take immediate action to protect yourself

Work together with ethical experts
Your challenges
How to gain access to the dark web marketplaces: Many underground marketplaces where stolen credentials are sold are impossible to access without infiltration. This requires specialized effort and expertise and a significant amount of time, making it challenging for you to effectively monitor for stolen credentials yourself.
How to engage with the dark web securely, legally and ethically: Engaging with the dark web or other illegal marketplaces to monitor for stolen credentials yourself can raise security, legal and ethical questions. This notably includes handling sensitive personal data stolen from your employees.
How to find the information that is relevant to you: The amount of information on the dark web is overwhelming. Criminals are constantly adding new data. Filtering through this to find the information that is relevant to your organization can be like searching for a needle in a haystack.
How we support you
We have a unique information position when it comes to the dark web: through infiltration of dark web marketplaces that operate out of sight, we have up-to-date knowledge of what is offered for sale there - specifically any stolen credentials originating from compromised systems.

Paul Pols
Security Lead
Secura
Dark web monitoring is the last line of defense before ransomware attackers can gain initial access to your network.
How Dark Web Monitoring works
01
Scope and baseline
Which (sub)domains do you want to monitor? The first step is to provide a baseline of information that is already available about your organization on the dark web. On that basis we will define the scope for future alerts.
02
Daily monitoring
We monitor the dark web daily for stolen credentials for your assets and compromised systems, to make sure that we stay up-to-date on intelligence.
03
Validation
Not all information is equally important, relevant or urgent. Our experts validate any new information that our monitoring shows.
04
Notifications and recommendations
If there is a serious threat, you receive an immediate notification. We provide insight into which accounts and systems have been compromised. You can expect help you to determine the best course of action, so that you can protect your organization from potential attackers.
Contact me
Would you like to know more about how our Dark Web Monitoring service can help you? Fill out the contact form and we will contact you within one business day.

Download brochure

Related

Trends in ransomware
Ransomware gangs are finding new ways to target their victims. Find out more about these changing tactics.

Limit your attack surface
Stolen credentials are only part of your external attack surface. The External Attack Surface Assessment also looks at exposures and vulnerabilities.
Become resilient against ransomware
How resilient is your organization when it comes to ransomware? The Ransomware Resilience Assessment looks at this question in depth.
Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.





