How we created the WI-FI backpack to help Pentesters and Red Teamers
What do you do as a hacker if you need a device that doesn't exist? You make it yourself... We created the WI-FI backpack to help us gain access to targets' WI-FI networks.
... > Vulnerability Assessment / Penetration Testing (VAPT) > Developing the Wi-Fi Backpack
The idea behind the WI-FI Backpack
Whether you are a penetration tester or a red teamer, you will often find yourself in need of an effective solution to efficiently gain access to your target’s WI-FI network, as it can provide an interesting entry point that is often overlooked.
However, the solutions offered by different vendors were often lacking in one area or another. Most devices on the market that we came across had a catch, such as coverage that was too weak for our intended purposes, lack of support of multiple wireless bands, and so on.

That's why we came up with the idea of rolling up our sleeves and doing it “the hacker way” and creating our own device. Enter the WI-FI Backpack.

Amir Saad
Security Specialist
Secura
We try to always be creative: if it doesn't exist, we will make it ourselves
The WI-FI backpack design
If you want to gain access to a target's WI-FI, the ideal device needs to meet a number of requirements. So when we started off with the design, we gathered a list of requirements that addressed the shortcomings of the devices that were being offered on the market. Our new device should be:
- Modular
- Discrete
- Efficient
- Capable of wide coverage
- Covers both 2.4 and 5.0 GHz bands.
Let us find out how we have addressed each of those requirements, and how they all came together to form our final device.
01
Modularity
To make the device as sustainable, scalable, and as future-proof as possible, we selected a modular design in which the antennas can be exchanged with other weaker/stronger ones, or if an engagement calls for a different type of antenna, such as directional VS. Omnidirectional.
This would also mean that if better Wi-Fi adapters were to be released, we would be able to effortlessly incorporate them within our device, and the same goes for the main component, the Raspberry PI.
02
Discreteness
The device needs to be usable in red teaming engagements. So understandably, we can’t walk around with a large machine with blinking lights and big antennas sticking out while on a client’s premise.
That is why we selected a discrete form factor for the device. One that can easily fit in a backpack (hence the name), a suitcase, or a fanny pack (if you’re a fan of those).
03
Efficiency
Efficiency can be defined as performing the most amount of work with the least amount of time. Which was one of the main goals during the design phase of our device.
For this purpose, we’ve written the software that ties everything together with the intention of achieving the most impact with the least amount of interactions. And as an added bonus, this design also allows operators with little to no experience with wireless security be able to use the device effectively.
04
Coverage
As red team operator working on a physical intrusion scenario, the last thing you’d want is to miss a potential initial access vector because of a network on the other side of the building that your regular device just did not pick up. For that reason, the device can carry up to four high-powered omnidirectional antennas that guarantee a long range of coverage and support for 2.4 and 5 GHz Bands.
05
Command and control
To achieve the goal of portability and efficiency, we have concluded that the best way to operate the device was through the operator’s phone. That way, operation would be stealthy and fast since the operator would not need to spend too much time on their phone to carry out an attack or fumble with a strange looking device during their engagement.
For that reason, a web interface was created which granted full control to the operator.
Details on Command and control
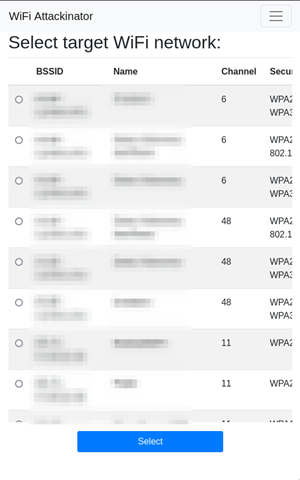
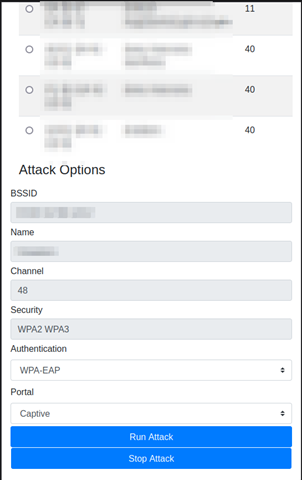
The device allows the operator to connect to it wirelessly using any mobile device they have on hand. This gives them access to an interface where they can select target networks, choose an attack, and edit its parameters, then launch that attack with a single button.
Whether it is a death-handshake capture combo, an evil twin attack, or even an enterprise network attack, the device would now begin the attack in the background and notify the operator when the attack is complete.
The device is also capable of carrying out attacks on enterprise Wi-Fi networks, in addition to evil twin attacks where a malicious copy of an access point is created with the goal of overpowering the original one, tricking the target client into connecting and authenticating to it.
The operator then would be able to capture the credentials used in the authentication process and use them to further their access into the network.
And, does it work?
Yes, it works! In addition to being a fun project to work on, it had been used to successfully obtain initial access in multiple Red Team and wireless network assessments. Something that had made some of our clients request it by name.
The WI-FI Backpack was a result of a joint effort between multiple consultants at Secura who had a mentality of creating a way if there were not any available at the time. So, it is on to the next challenge.
Contact us
Do you want more information on our pentesting services and expertise? Fill out the form and we will contact you within one business day.

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.





