EUCC - Certification of ICT Products in Europe
A fresh approach to certifying information and computer technology (ICT) products.
... > Common Criteria > EUCC - A New Cybersecurity Scheme for the Certification of ICT Products in Europe
EUCC - A NEW CYBERSECURITY SCHEME FOR THE CERTIFICATION OF ICT PRODUCTS IN EUROPE
The European Union Cybersecurity Certification (EUCC) represents a fresh approach to certifying information and computer technology (ICT) products within Europe, updating the previous SOG-IS Mutual Recognition Agreement (MRA) framework.
EUCC is founded on the Common Criteria (CC) certification scheme, which integrates internationally recognized innovative concepts to meet stakeholders' needs, including enhanced provisions for patch management, vulnerability management and vulnerability disclosure in certified products.
CC (Common Criteria)
The CC (Common Criteria) denotes an international set of standards, guidelines, and criteria used for evaluating the security capabilities of various products and systems. Originally developed to ensure that technological offerings comply with specific security benchmarks and governmental directives, CC serves as a benchmark for assessing the efficacy and accuracy of security measures.
By defining assurances based on measurements of effectiveness and accuracy, CC serves as a bulwark against prevalent cybersecurity challenges such as data breaches, information leakage, and privacy infringements.
Following rigorous scrutiny and thorough assessment by expert evaluators, technology products deemed to meet the requisite standards are bestowed with a recognized CC Certification.
Grasping the fundamental principles and underlying rationale of CC is imperative for comprehending universally applicable cybersecurity protocols and deciphering the novel EUCC initiative.
EUCC
The EUCC scheme builds upon the core elements of CC, extending its application to technology products within the European Union. EUCC introduces supplementary criteria alongside the established CC and Common Methodology for Information Technology Security Evaluation (CEM) [5] protocols.
Enhancements to cybersecurity certifications involve heightened oversight and management of compliance measures, greater transparency through the dissemination of vulnerability information to the public, and expanded consumer assistance, such as comprehensive patch management services for certified products.
EUCC is implemented for ICT products that:
- Incorporate a significant array of security functional prerequisites outlined in CC Part 2 [3].
- Strive to attain a 'substantial' or 'high' level of assurance for the EU Cybersecurity Act (CSA) components encompassed by EUCC.
EUCC comparison with existing schemes
Evaluation criteria and methods for ICT products
To meet EUCC compliance, Security Targets (STs) must include the following CC requirements, regardless of their assurance level or associated dependencies:
- At least one AVA_VAN component.
- At least one ATE_IND component.
For EUCC certificates rated at the 'substantial' assurance level, the certificates must encompass AVA_VAN level 1 or 2. For certificates rated 'high' assurance level, coverage of AVA_VAN level 3, 4, or 5 is required.
Certification of ICT products at AVA_VAN levels 4 or 5 is restricted to specific scenarios:
- If the product belongs to a technical domain listed in Annex I of the EUCC Regulation [1], it is evaluated according to the state-of-the-art documents of those domains.
- ICT products within categories covered by Certified Protection Profiles (PPs) with AVA_VAN levels 4 or 5 listed in Annex II of the EUCC Regulation [1] undergo evaluation following the specified methodology outlined for those PPs.
- In exceptional cases where a technical domain or PP is not listed, certification at these levels is possible with thorough justification and approval processes by National Cybersecurity Certification Authorities (NCCAs) and the European Cybersecurity Certification Group.
Note: EUCC does not acknowledge Common Criteria Recognition Arrangement (CCRA) certificates for PPs. Therefore, the evaluation of STs claiming conformity to CCRA/non-EUCCPPs will consider the PP content non-evaluated.
Note: ENISA should provide the list of certified PPs on its cybersecurity certification website and indicate their status, in accordance with Regulation (EU) 2019/881.
Information necessary for certification
Apart from the Target of Evaluation (TOE) required by the CC, applicants must also provide:
1) A publicly accessible website containing the following information upon certificate issuance:
- Guidelines and suggestions help end users securely configuring, installing, deploying, operating, and maintaining ICT products or services.
- Duration of security assistance provided to end users, particularly regarding the availability of cybersecurity updates.
- Contact details of the manufacturer or provider, along with approved channels for receiving vulnerability reports from end users and security experts.
- Links to online repositories cataloging publicly disclosed vulnerabilities related to the ICT product, service, or process, as well as relevant cybersecurity advisories.
2) Vulnerability management and disclosure procedures facilitating compliance with the obligations outlined in Chapter VI of the EUCC Regulation [1].
Note: all documentation pertaining to the TOE certificate must be retained for a minimum of five years, including a sample of the certified product.
Conditions for issuance of an EUCC certificate
The vendor must agree to undertake the following obligations:
- Furnish the certification body and the IT Security Evaluation Facility (ITSEF) with all necessary, accurate, and complete information, and provide additional details upon request.
- Refrain from marketing the ICT product as EUCC certified until the EUCC certificate has been officially issued.
- Market the ICT product as certified only within the parameters outlined in the EUCC certificate.
- Immediately halt promotion of the ICT product as certified in case of EUCC certificate suspension, withdrawal, or expiration.
- Ensure that any ICT products advertised as EUCC certified are exactly identical to those subjected to certification.
- Adhere to the prescribed rules governing the use of the EUCC certificate's mark and label, as outlined in Article 11 of the EUCC Regulation [1].
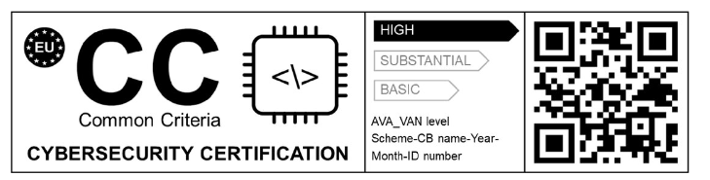
Figure 1: The form of EUCC mark and label [1]
Note: The use of new EUCC mark and label on the certified product is voluntary.
Opting for a Certification Body (CB) and ITSEF
Commercial CBs will conduct certification at the substantial assurance level (AVA_VAN.n; n<3). It's anticipated that most existing ITSEFs will transition into CBs for the substantial level. For substantial assurance level, the typical procedure involves selecting a provider capable of conducting both evaluation and certification.
Evaluating and certifying at the high assurance level (AVA_VAN.n ; n>2) requires NCCAs to authorize both ITSEFs and CBs. The existing SOG-IS CBs are expected to obtain authorization status. For the high assurance level, it is customary to engage a governmental CB along with an authorized ITSEF under their purview, contingent upon the technical domain and applicable PP.
Management of the EUCC Evaluation and Certification Process
The implementation of the EUCC evaluation and certification process will closely resemble current practices under SOG-IS, with individual CBs and ITSEFs establishing their contractual terms.
The EUCC assigns specific actions and responsibilities to ITSEFs and CBs regarding compliance monitoring (Chapter V of the EUCC Regulation [1]), which are typically incorporated into contractual agreements with certificate applicants.
Post-Acquisition Obligations of EUCC Certificate Holders
Following the issuance of the EUCC certificate, in addition to upholding the commitments stipulated in Article 9 of the EUCC Regulation [1], certificate holders are mandated to implement the following processes and activities throughout the certificate's duration:
- Regularly monitor vulnerability intelligence concerning the certified TOE (Article 27 of the EUCC Regulation [1]).
- Provide assistance in rectifying non-compliances (Article 29 of the EUCC Regulation [1]).
- Handle and disclose vulnerabilities impacting the certified TOE (Chapter VI of the EUCC Regulation [1]).
Monitoring Responsibilities of EUCC Certificate Holders
The EUCC certificate holders must undertake the following actions to ensure the certified ICT product's adherence to their security standards:
1) Be aware of vulnerability information concerning the certified ICT product, which involves monitoring known dependencies through internal means, as well as considering:
- Publications or disclosures of vulnerability information by end users or security researchers, as outlined in Article 55(1), point (c) of Regulation (EU) 2019/881;.
- Submissions from any other relevant sources.
2) Closely follow the level of assurance articulated in the EUCC certificate.
Furthermore, it is mandatory for the certificate holder to collaborate with the CB, the ITSEF, and, if applicable, the NCCA to assist in their monitoring endeavors.
Assisting in Rectifying Non-Compliances
Should a non-compliance issue arise that impacts either the TOE or the certificate holder, the procedures outlined in Articles 28 and 29 of the EUCC Regulation [1] delineate the necessary course of action. Failure to address these issues may result in the suspension or withdrawal of the certificate.
The holder of the EUCC certificate is obligated to initiate remedial measures within 30 days.
Vulnerability Oversight and Disclosure
Chapter VI of the EUCC Regulation [1] outlines the essential procedures for managing and disclosing vulnerabilities that must be adopted by EUCC certificate holders. While the EUCC does not prescribe specific timelines for these processes, it adheres to the principle of avoiding undue delays.
Two associated standards, EN ISO/IEC 30111 [6] and EN ISO/IEC 29147 [7], are referenced as beneficial for aiding these processes, although they are not obligatory.
Certificate Maintenance
The EUCC provides the following options to maintain a certificate:
Re-assessment
If it becomes necessary to evaluate the effects of alterations in the threat landscape on an unmodified certified ICT product, a request for re-assessment must be forwarded to the CB. The ITSEF will conduct this re-assessment, leveraging all pertinent findings that remain applicable. This procedure may result in the EUCC certificate being extended, affirming or revising the prior level of assurance.
Changes to a certified ICT product
This procedure resembles the SOG-IS concept of "Assurance continuity," although it differs in that it does not provide explicit criteria for categorizing changes as either minor or major.
Patch management
Patch management mechanisms and procedures must be included in the assessment and certification scope in the following cases:
- When the affected functionalities by the patch are situated outside the certified ICT product's TOE.
- When the patch pertains to a predetermined minor modification to the certified ICT product.
- When the patch addresses a confirmed vulnerability, with significant implications for the security of the certified ICT product.
The patch management protocol for an ICT product comprises the following components:
- The procedure for developing and releasing patches for the ICT product.
- The technical mechanisms and functionalities for integrating patches into the ICT product.
- A series of assessment activities concerning the effectiveness and performance of the technical mechanisms.
However, the patch management option does not apply to addressing non-critical vulnerabilities, which should be handled in accordance with Article 13 of the EUCC Regulation [1].
The legislative transition process
The EUCC regulation will be enforced starting from February 27th, 2025. Within 12 months from this date, the existing national cybersecurity certification schemes will discontinue their activities. It's important for vendors to know that any certification procedures initiated within the subsequent 12 months of the legislation coming into effect must be completed by no later than February 2027.
Security Functional Requirements (SFRs) and Security Assurance Requirements (SARs)
The new EU CC certification can be implemented on top of both the older and newer versions of the Common Criteria standard. From that point of view, there is no change for SFRs and SARs based on CC Part 2 [3] and CC Part 3 [4], as the EU CC scheme builds upon the core elements of CC and introduces supplementary criteria alongside the established CC and Common Methodology for Information Technology Security Evaluation (CEM) [5] protocols. Of course, between the older (CC V3.1) and the newer (CC:2022) versions of the Common Criteria, there are differences in terms of the SFRs and SARs, which developers and laboratories need to consider.
Note: It is possible that changes regarding SFRs and SARs could be published by the EUCC in the future.
REFERENCES
[1] COMMISSION IMPLEMENTING REGULATION (EU) 2024/482 of 31 January 2024 laying down rules for the application of Regulation (EU) 2019/881 of the European Parliament and Council regarding the adoption of the European Common Criteria-based cybersecurity certification scheme (EUCC)
[2] [CC Part 1] Common Criteria for Information Technology Security Evaluation Part 1: Introduction and general model
[3] [CC Part 2] Common Criteria for Information Technology Security Evaluation Part 2: Security functional components
[4] [CC Part 3] Common Criteria for Information Technology Security Evaluation Part 3: Security assurance components
[5] [CEM] Common Methodology for Information Technology Security Evaluation, Evaluation methodology
[6] ISO/IEC 30111:2019 Information technology Security techniques Vulnerability handling processes
[7] ISO/IEC 29147:2018 Information technology Security techniques Vulnerability disclosure
Acronyms
CB |
Certification Body |
CCRA |
Common Criteria Recognition Arrangement |
EU |
European Union |
EUCC |
European Common Criteria-based cybersecurity certification scheme |
ICT |
Information and communication technology |
ITSEF |
Information security evaluation facility |
NCCA |
National Cybersecurity Certification Authority |
CSA |
EU Cybersecurity Act |
CEM |
Common Methodology for Information Technology Security Evaluation |
PP |
Protection Profile |
SOG-IS |
Senior Officials Group Information Systems Security |
ST |
Security Target |
TOE |
Target of Evaluation |
RELATED SERVICE
Contact Us
Would you like to learn more about our Common Criteria Certification service for your organization? Please fill out the form and we will contact you within one business day.

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.







