
Security concerns in popular smart home devices
As smart houses become more popular, Secura has developed an IoT hacking demonstration kit in the form of a smart house. This article describes several of the vulnerabilities our experts discovered in the devices that are used within the kit.
Safety risks in common smart home devices
Smart houses are becoming ever more popular. That's why Secura developed an IoT hacking demonstration kit in the form of a smart house: it is a miniature house, outfitted with several popular smart home gadgets. We discovered several vulnerabilities in the devices that are used in the demonstration kit. This article details several of these findings.
Note: Prior to publishing this article, multiple attempts were made to inform the (re)sellers and Original Equipment Manufacturer (OEM) about the discovered vulnerabilities and the consequences that come with it. One of the (re)sellers did not respond to any email communication attempts but was reached by phone once. Thereafter, no further responses were received. The other (re)seller provided us with their manufacturer. However, Secura never received any further responses after informing them about the vulnerabilities. Secura has chosen to publish this article to enhance security awareness among manufacturers and users.
The products that are covered in this article were selected by visiting popular web shops within the Netherlands, and thereafter filtering on popular devices. We only mention vulnerabilities that resulted into disabling, or bypassing the main security features of the products in this article.
Flient Smart Lock
One of the two products that will be covered within this article is the ‘Flient Smart Lock’, which is a smart door lock that can be opened in multiple ways. A non-exhaustive list is stated below:
- NFC tags
- Mobile application (Bluetooth Low Energy)
- Biometrics (Fingerprint)
- Key Pad (Key combination)
The mobile version that was used along side of the door lock was:
com.tongtongsuo.app versionName=6.7.0 versionCode=234
Two serious security concerns were discovered for the Flient Smart Lock.
1. Biometrics bypass
The first security concern that was discovered was that an attacker could replace the stored fingerprints within the lock (CVE-2023-50124). This ultimately results in an attacker being able to gain unauthorized access to the perimeter.
As mentioned before, the Flient Smart Lock allows users to unlock the door via a biometric fingerprint. The figure stated below shows (from an application perspective) how the user had a fingerprint set on the door:

The fingerprint scanner is an AES1711 scanner, which is located within the door handle of the lock.
However, it turned out that there are two screws accessible from the outside of the door, which can be removed by an attacker to get access to the fingerprint sensor:

Once the screws were removed, the sensor was extracted from the lock and connected to an analysis workstation:
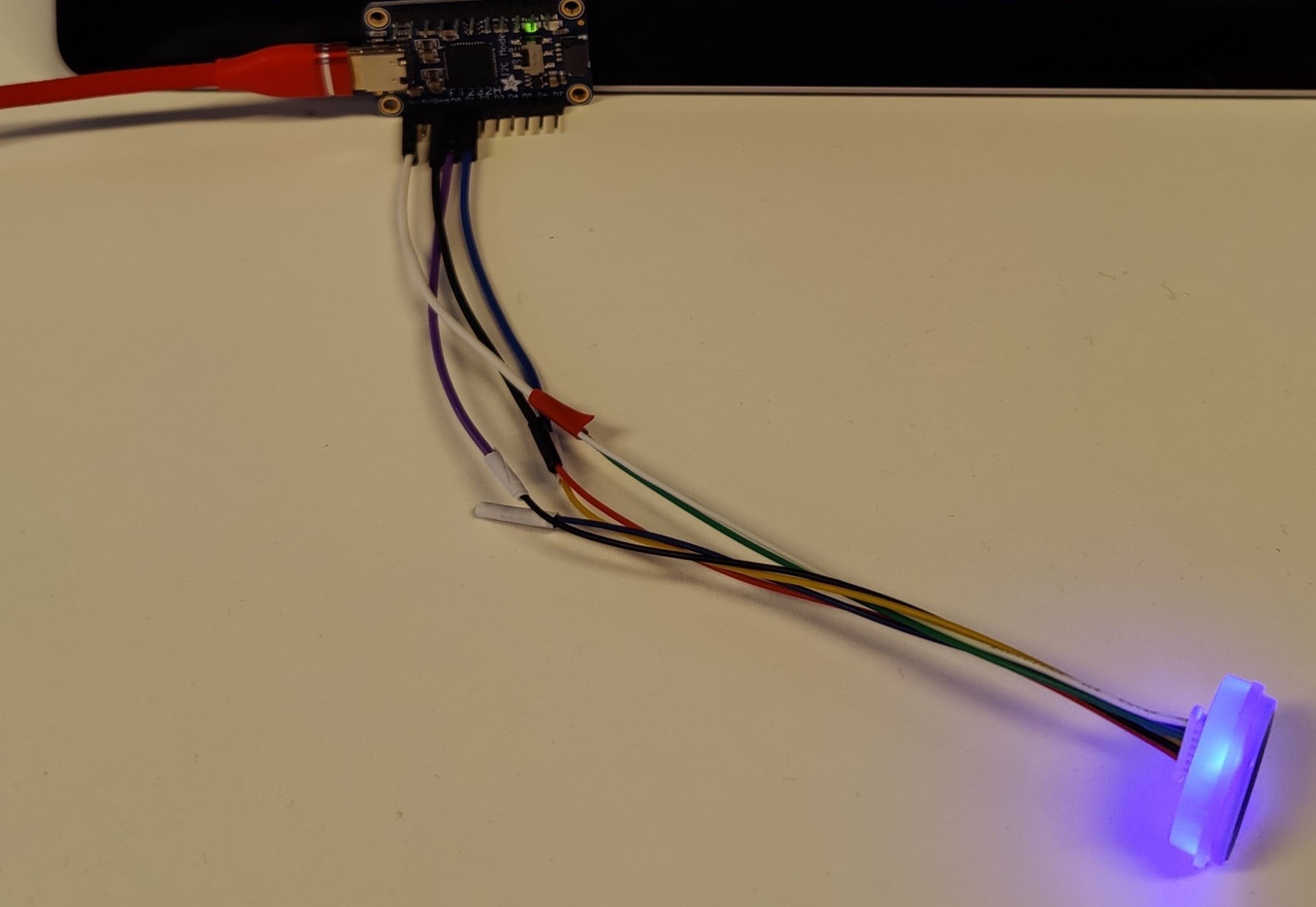
Due to the fact that a default password was set on the UART interface, a new fingerprint could be placed on the sensor. See the below stated figure:
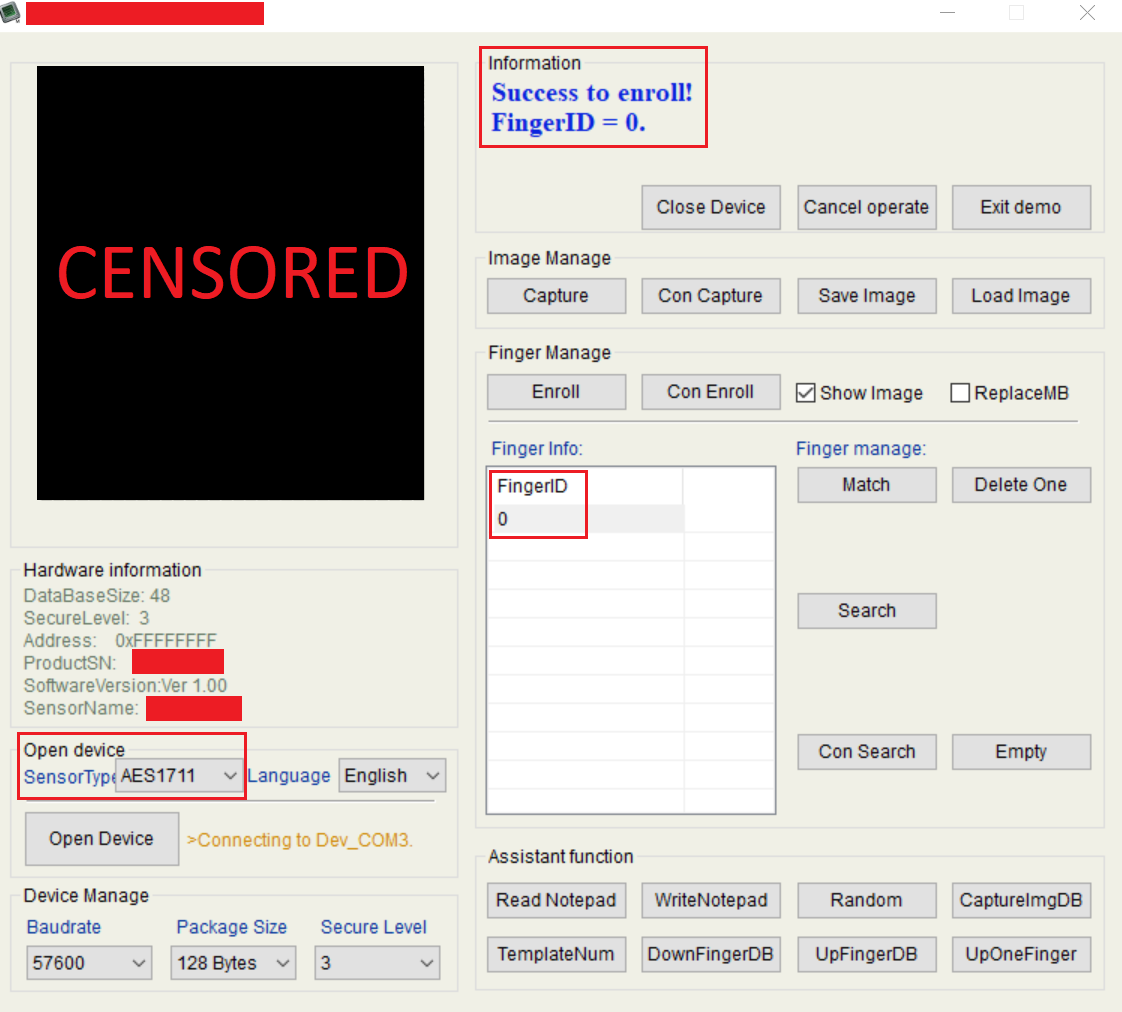
Once the fingerprint was replaced, the sensor was placed within the door handle again, and it was tested whether the regular user could still open the door. The below stated figure demonstrates how a regular user (indicated on the left side) now was unable to open the lock. On the right side of the below stated figure is shown how the product reacted to the new fingerprint set by the attacker. As can be seen, the door could be unlocked (indicated by the green light that is shown).

This attack was successful due to the fact that the smart lock simply verifies whether the finger provided to the scanner matches one of the stored fingerprints, which an attacker is able to replace.
This attack can be performed by an attacker in approximate five minutes and allows an attacker to gain access to the perimeter.
2. Cloneable Tags
The second security concern that was discovered within the lock, was that the provided tags that come with the purchase can be cloned by an attacker (CVE-2023-50129).
One of the NFC tags was scanned, which provided the following results:
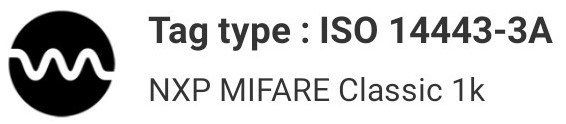
Note how the tag is categorized as MIFARE Classic 1K.
A second tag was scanned and a comparison was made:
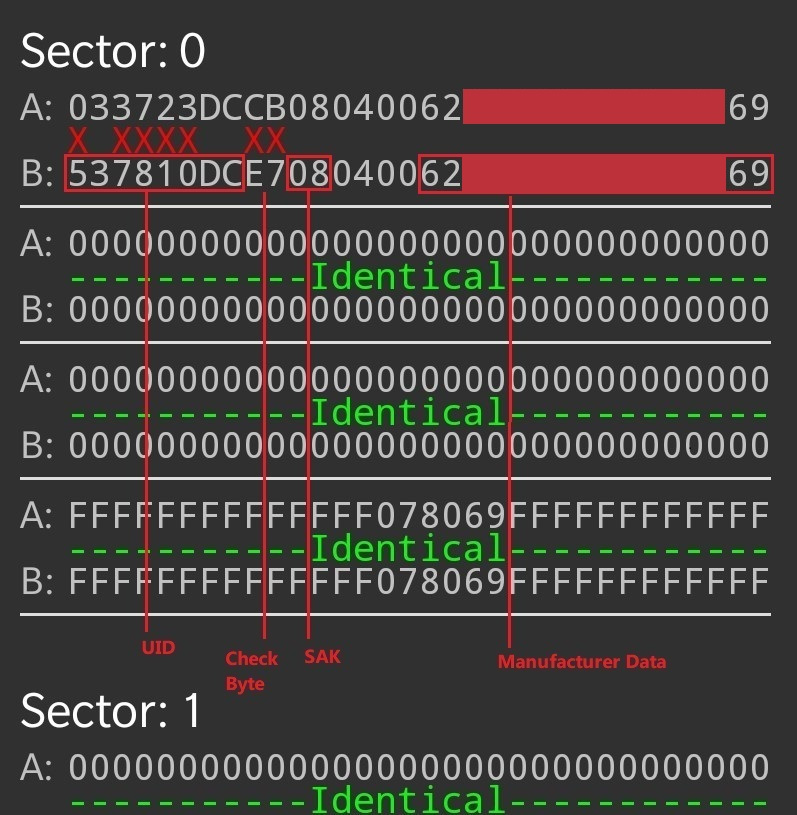
The only deviations that were observed were within Sector 0. All other sectors were empty.
In order to demonstrate the easiness of cloning these kind of MIFARE Classic 1K tags, the tag was held against a Flipper Zero.
Thereafter, the Unique Identification Number (UID) was emulated on the Flipper Zero and held against the door lock. This resulted in the door being unlocked:

Thus, concluding that only the UID is required in order to open the door lock.
This means that the tags only use identification, instead of identification in combination with authentication.
Secura recommends the vendor to consider replacing the MIFARE Classic 1K tags with tags that make use of the latest MIFARE DESFIRE.
Hozard® Alarmsysteem
The second device in which we discovered vulnerabilities is the 'Hozard® Alarmsysteem', which is a smart alarm system. We discovered three concerning issues with this device.
The system can be set to an armed or disarmed stated in multiple ways:
- SMS functionality
- Mobile application
- RFID Tags
- Remote control
The mobile version that was used along side of the alarm system was:
com.tuya.smartlife versionName=5.2.2 versionCode=558
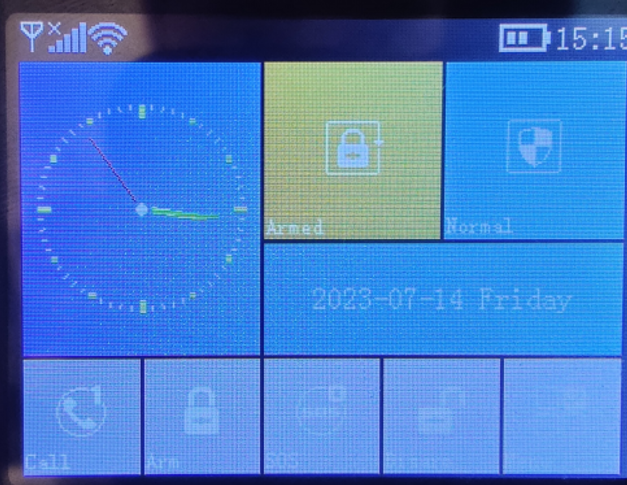
Whenever the alarm system is in an armed state, meaning that it will
trigger once a sensor detects any kind of motion, it looked as
follows:
1. SMS functionality concerns
If an attacker obtains the phone number of the alarm system, they can send a command from a random phone number (CVE-2023-50127). It is not needed to spoof the phone number of the end-user.
There are two main methods for an attacker of retrieving the phone number associated to the alarm system:
- Retrieving the sent SMS message from the mobile phone of the end-user.
- Intercepting SMS traffic whenever the end-user sends a SMS message.
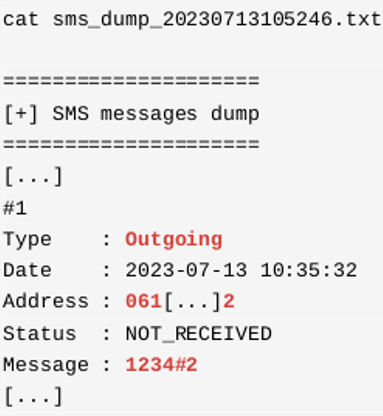
An example of an attacker dumping the sent SMS messages, in order to retrieve the phone number and disable command, from an infected mobile device is given below:
The other method is to intercept the SMS traffic whenever the end-user sends a SMS message.
A simplified overview of such an attack scenario is given below:
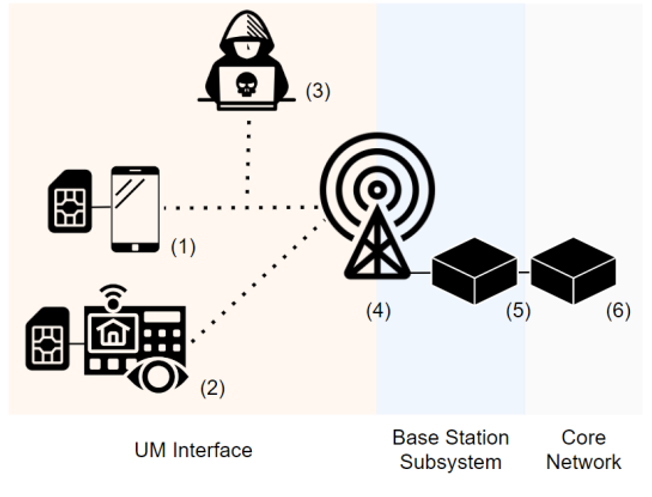
- Mobile Station (MS)
- The alarm system
- An attacker within a close proximity of the MS, sniffing the communication with specialized equipment.
- Base Transceiver Stations (BTS)
- Base Station Controller (BSC)
- Mobile Switching Center (MSC)
However, as to not overcomplicate things, let’s consider that an attacker already managed to retrieve the phone number of the alarm system.
An attacker can send the following SMS command, which contains a default engineer password (CVE-2023-50125), to gain system information about the alarm system:
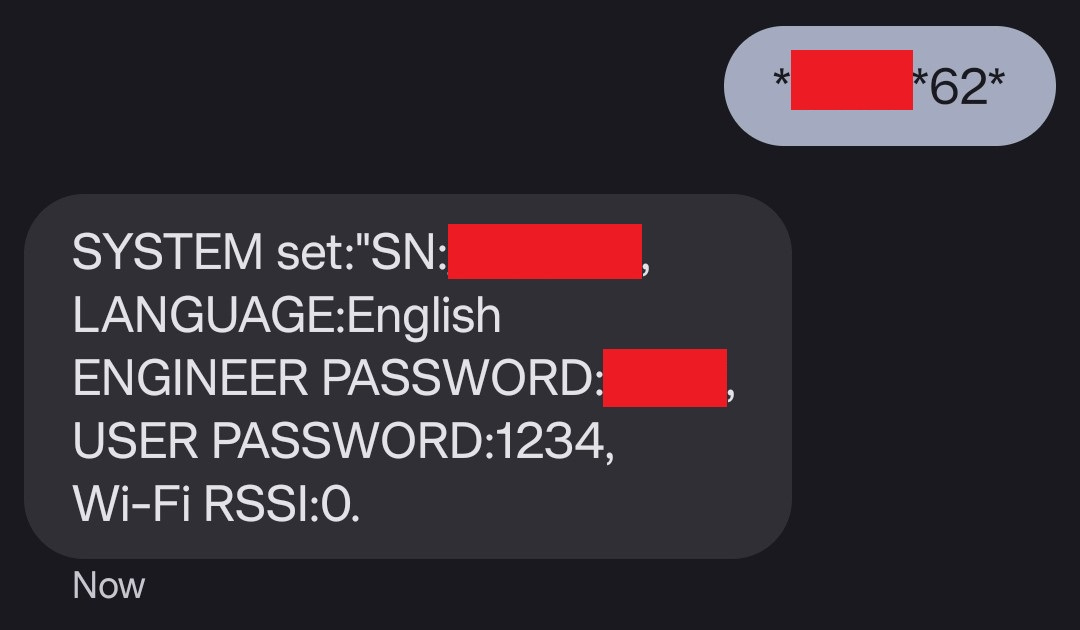
Please note that the engineer password is not forced to be changed during the initial setup of the device, and that the settings to alter the password are located within a menu that is not easy to discover for a regular user.
After this, an attacker can send a SMS command to bring the alarm system to a disarmed state:
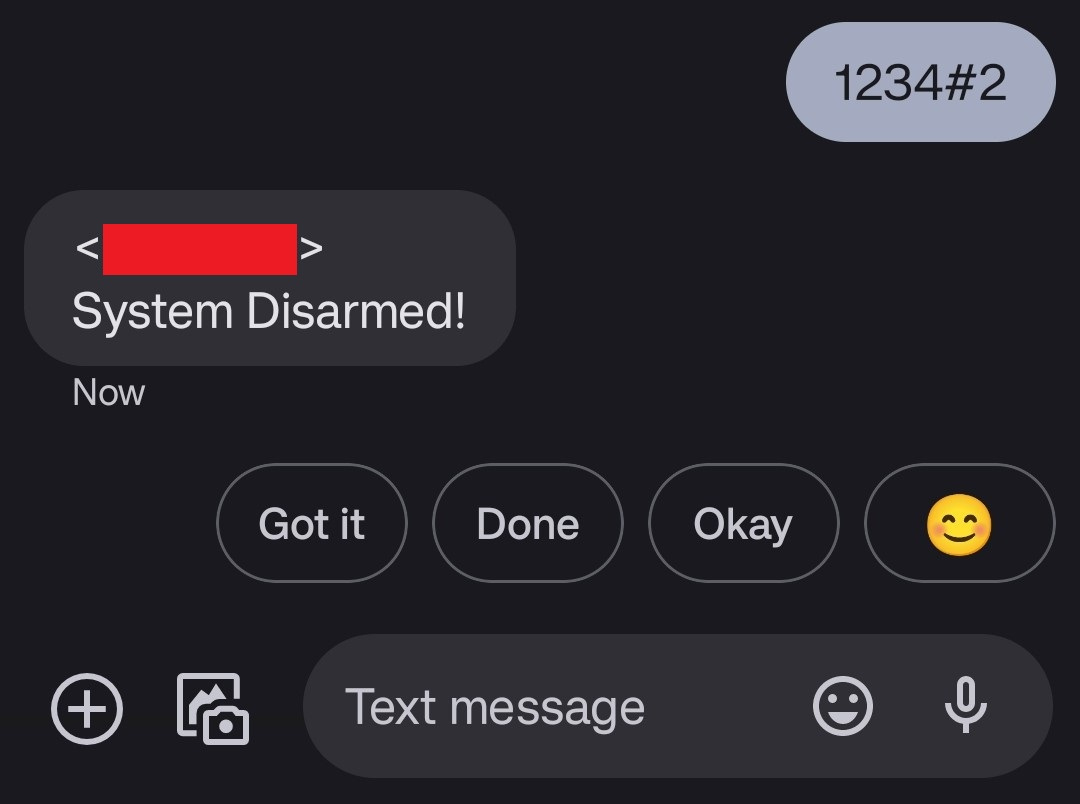
Even if an attacker would not be able to retrieve the user password via the default engineer password, they could simply send multiple attempts to the alarm system until they guess the correct one (CVE-2023-50123).
This allows an attacker to disable the alarm system remotely:
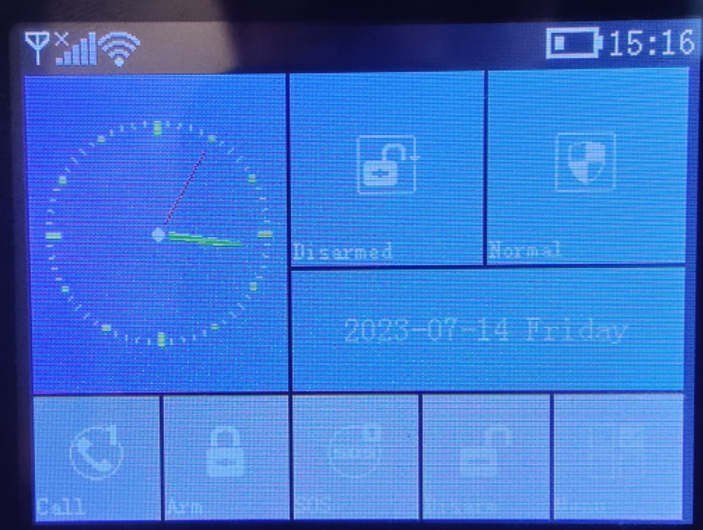
This means that an attacker can access the perimeter without triggering the alarm system.
2. Replayable remote control signal
The alarm system also comes with a remote control, which allows a user to bring the alarm to an armed, or disarmed state.
Within the user manual of the alarm system, there is stated that the remote control operates on a well-known frequency band. This was verified by conducting a spectrum analysis when pressing the disarm button on the remote control:
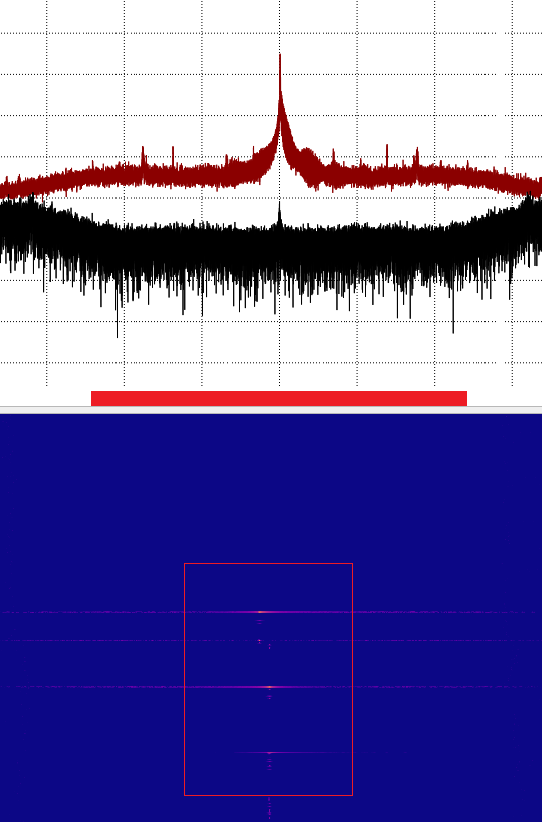
As can be seen in the above stated figure, the spectrum analyzer showed activity on the frequency whenever a command was sent.
For the sake of simplicity, and to demonstrate that limited technical knowledge is required by attackers, the Flipper Zero was used again for the proof of concept.
Each time the saved file was replayed, it resulted in bringing the alarm system to a disarmed state (CVE-2023-50128). Thus, concluding that no rolling code mechanism is implemented within the alarm system. This allows an attacker who is able to intercept the disarm command once, to bring the alarm system to a disarmed state whenever they desire.
3. Cloneable Tags
Although the research is conducted in a slightly different manner, the underlying issue of the RFID tags (CVE-2023-50126) are similar to the NFC tags (which is a subset of RFID) of the smart door lock. See the 'Cloneable Tags' section of the smart door lock for more information about the underlying issue.
Conclusion
This article has shown how tech-savvy burglars can make use of insecure smart devices to gain access to a smart home. Most of the discovered vulnerabilities can easily be exploited by attackers who have little to no technical knowledge, due to the Flipper Zero.
Contact me
Do you want more information on IoT testing on consumer products? Please fill out the form below and we will get back to you in one business day.

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.





