OT Perimeter Assessment Step 1: network design
Where to start with OT security? The OT Perimeter Assessment is a good start. This article explains in depth how our OT security specialists construct an overview of your design network and map possible threats.
... > OT Perimeter Assessment > OT Perimeter Assessment step 1: network design
Why the connection between IT and OT is so risky
Traditional notions of Operational Technology (OT) networks as isolated no longer reflect reality. In today's landscape, OT networks intertwine with IT networks, exposing them to all kinds of threats. Most cyber attacks begin in the IT or external networks. Attackers then exploit vulnerable connections and infiltrate the OT side. Addressing these threats and securing the perimeter is often the most important step when it comes to OT security.
Where to start with securing your OT
Operational Technology environments are complex and difficult to secure. Assessing your whole network at once or chasing full compliance towards IEC 62443 can seem like an unachievable goal. Where do you start?
A good starting point is the OT Perimeter Assessment. It focuses on securing all connections between the OT systems and all external networks. The assessment itself consists of three important steps: reviewing the network design, firewall configuration analysis and traffic- and system scans.
This article covers the first step: The network design. How exactly do we pinpoint threats using your network design? And what’s in it for you?
Constructing a network illustration
The first thing we do when conducting an OT Perimeter Assessment, is to define the project's scope, always in consultation with you, the client. What exactly is your OT network and how is it interconnected? We analyze the network by studying documents like network drawings, asset registers and firewall configurations, even though this information might be incomplete or outdated.
Using these documents, we then create an initial data flow diagram (DFD), mapping essential systems in the connection between IT and OT networks. A DFD is a high-level representation of the network that we can use to map out all interconnectivity between different trust zones, like IT, OT or external zones like vendors or cloud applications. This diagram also illustrates the separation between various zones and systems in the IT and OT networks, following the structure of the Purdue model.
This is an example of a data flow diagram:

Once this diagram is complete, we use it during interactive sessions with your experts. The goal of these sessions is to verify or complement the DFD by comparing it to the actual situation and to review all known communication flows.
Identifying the threats
Once we have a thorough insight into the network design, it’s time to review all potential threats and entry points from and to the OT networks. To do this, we take an inside-out approach. We start from the connection point of the IT and OT networks (level 3.5 in the Purdue model) and move outward to assess the IT network (level 4 and 5) as well as the OT network (level 1, 2, and 3).
This sounds rather abstract, which is why we will use a few examples to highlight a few specific systems in this network diagram and examine the various threats that may affect these systems.
Threat 1: the risk of permissive access control
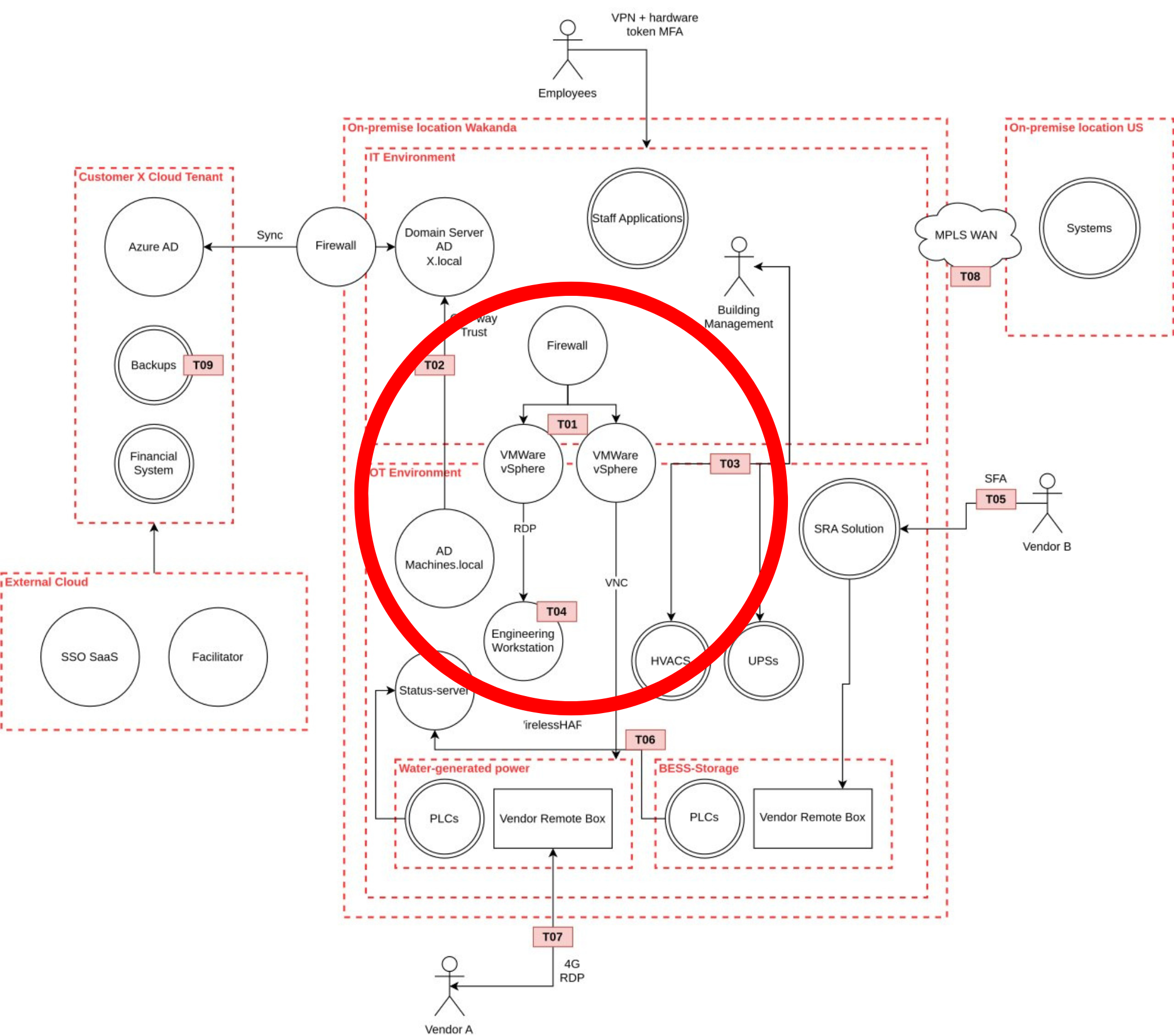
In the network diagram, marked at T01, we can see that there are multiple dual-homed systems connected both to the IT (firewall) and OT network. These systems have two separate network interface cards (NICs): one in the IT and one in the OT network. Operators and engineers commonly use these systems to access the OT network using a remote desktop application running on a virtual environment.
In this particular scenario, the dual-homed systems operate on VMware Vsphere: a complete virtual environment that virtualizes networks, desktops, and hardware for enterprise users. It is common to employ VMware for compartmentalization, ensuring that engineers and operators only have access to specific environments.
However, the role-based access control for some user groups to these environments may be too permissive, potentially posing a threat to the OT network when an attacker gains access to a user group. Another important question is whether the virtualization platform is dedicated for OT or shared with IT. We have sometimes seen that this gives the possibility to “break-out” of the operator environment and use this dual-homed system as a stepping-stone into the OT network.
More important is the attack surface of the hypervisor itself, the vSphere software. As this is often managed from the IT-side, the maintenance ports are accessible from the IT network. Weak configuration, outdated versions, poor passwords or the lack of patch management can result in multiple vulnerabilities with known exploits. Such exploits can enable an attacker to gain unauthorized access to these environments or to break out of the virtual environment after gaining initial access and ultimately gain access to the OT network or OT applications.
Threat 2: connection between OT systems and the IT Domain Controller
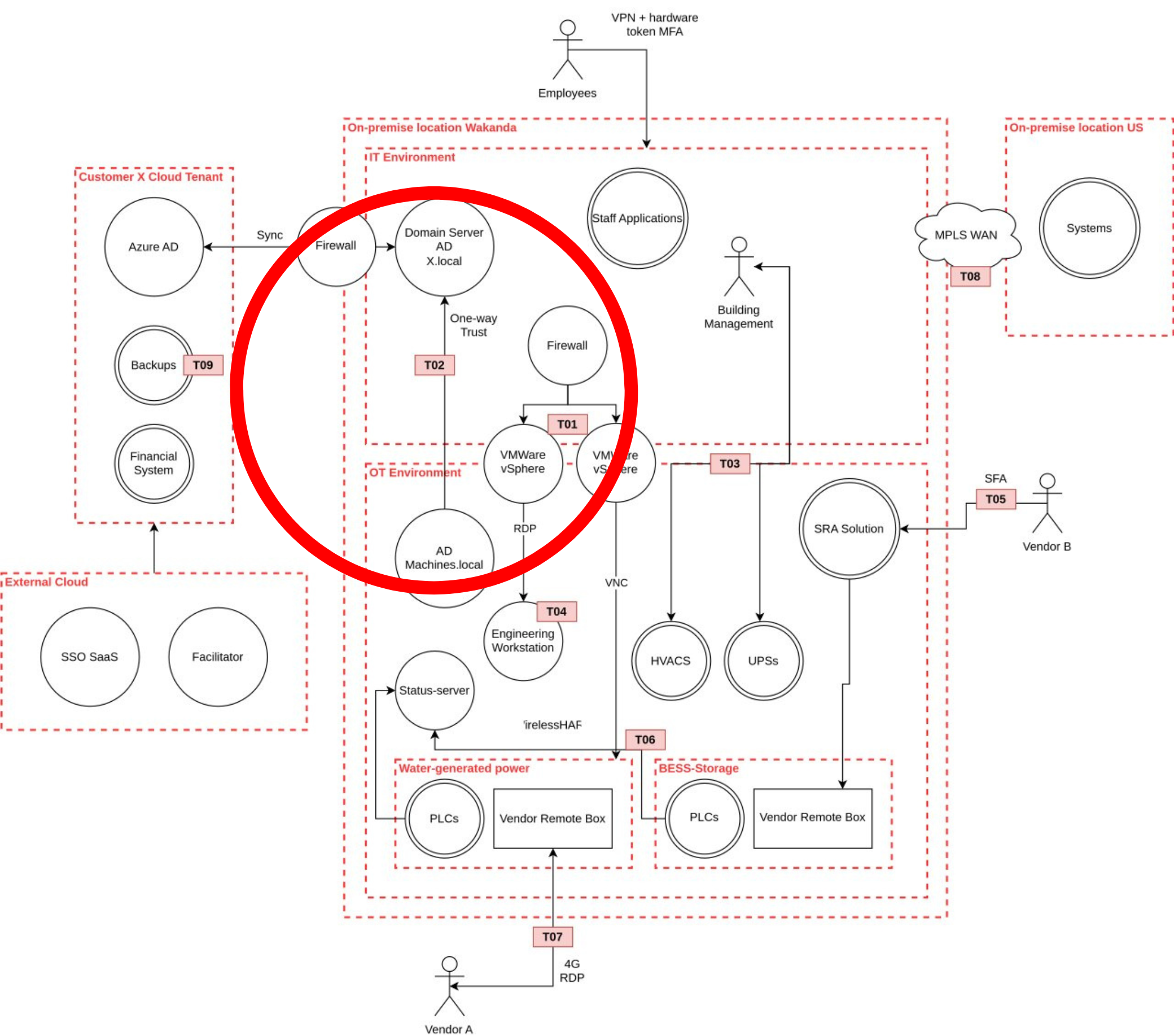
If we look at the T02 part of the diagram, we see another potential threat: the connection between OT systems and the IT Domain Controller (DC). This IT-server is responsible for managing all Active Directory (AD) authentication and domain-related activities. In this environment the OT Domain controller is connected to the IT DC using a trust relationship. This is convenient because all users can use the same credentials in both environments.
The trust relation might seem to be secure solution, but actually creates a serious attack surface on the OT-systems. When the IT AD accounts are compromised there is the immediate risk of unauthorized access to the OT network. Moreover, when the IT domain controller is abused to distribute ransomware, al domain joined systems will be compromised, in this case that would include all domain joined OT systems as well.
Finally, there are many communication ports required between the two domain controllers, many of which can be abused. Especially when the OT domain controller is patched less frequently, which is not uncommon in OT. By creating this connection, these vulnerabilities can be reached from the IT network. You might notice the absence of a firewall in this example, which would make the attack easier - but even with a configured firewall the attack vector is still there.
Threat 3: The HVAC and UPS systems in the OT zone
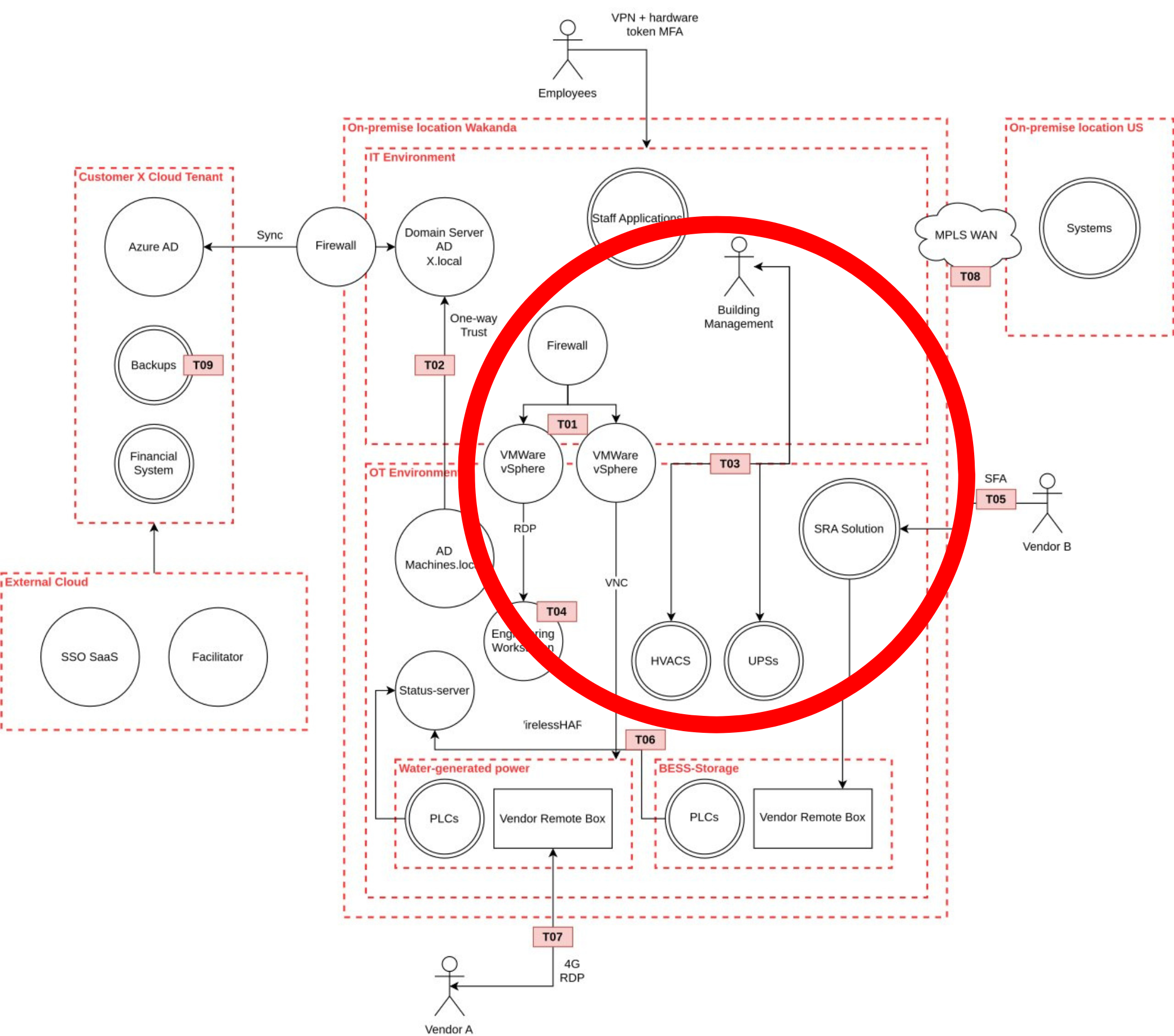
For the final example we look at T03 of the diagram: the HVAC and UPS systems in the OT zone. Although these systems are not directly connected to the OT network, they are often crucial to keep the Industrial control systems running.
However, in this case these systems are remotely manageable from a Building Management System (BMS) to monitor and maintain these systems. When these systems are poorly managed, maybe by a different department or even a remote third party, this could create another attack path from IT that can indirectly influence the OT systems, circumventing the IT/OT firewalls that are set in place.
How to improve your OT security?
These are just a few examples that show what kind of hidden weaknesses can be present in the current OT-network. Other examples might include (secure) remote access solutions used internally or by third parties, decentralized infrastructure with WAN connectivity, external cloud services, MES or ERP connections, data historians, equipment with web- or other remote interfaces, and many more.
Of course, the assessment does not stop at the design review, and the ultimate goal is to address the issues we just mentioned and to reduce your attack surface. The full OT Perimeter Assessment consists of:
- Understanding the network design
- Firewall configuration analysis
- OT system and network traffic scanning
In two upcoming articles, we will discuss the Firewall configuration analysis and the scanning parts of the assessment. In the meantime, you can read more information about the OT Perimeter Assessment, or you can download the brochure below.

OT Perimeter Assessment Brochure (ENG)
Read all about how the OT Perimeter Assessment can help you get started with OT security.
DownloadThe authors

Frank Ruedisueli
Principal OT Security Consultant

Abdulkarim Abdulkadir
OT Security Analyst

Tieke Jansen
OT Security Consultant
Contact us
Do you want to know more about the OT Perimeter Assessment or our OT security services? Please fill out the form and we will contact you within one business day.

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.







